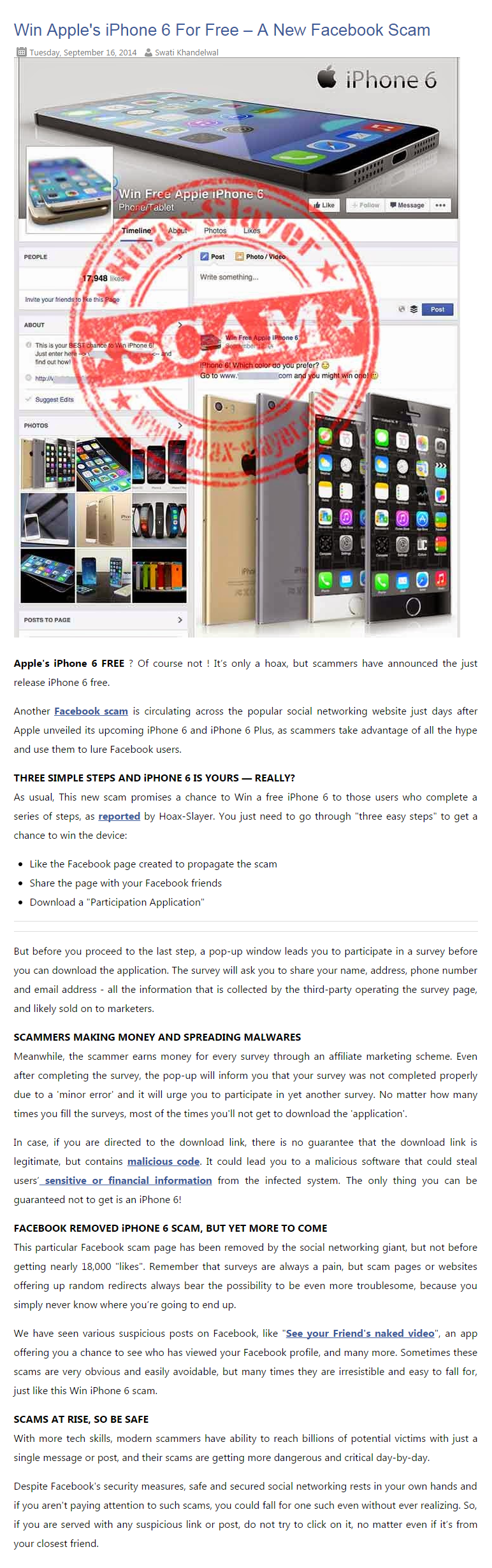
-
IP addresses are NOT logged in this forum so there's no point asking. Please note that this forum is full of homophobes, racists, lunatics, schizophrenics & absolute nut jobs with a smattering of geniuses, Chinese chauvinists, Moderate Muslims and last but not least a couple of "know-it-alls" constantly sprouting their dubious wisdom. If you believe that content generated by unsavory characters might cause you offense PLEASE LEAVE NOW! Sammyboy Admin and Staff are not responsible for your hurt feelings should you choose to read any of the content here. The OTHER forum is HERE so please stop asking.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
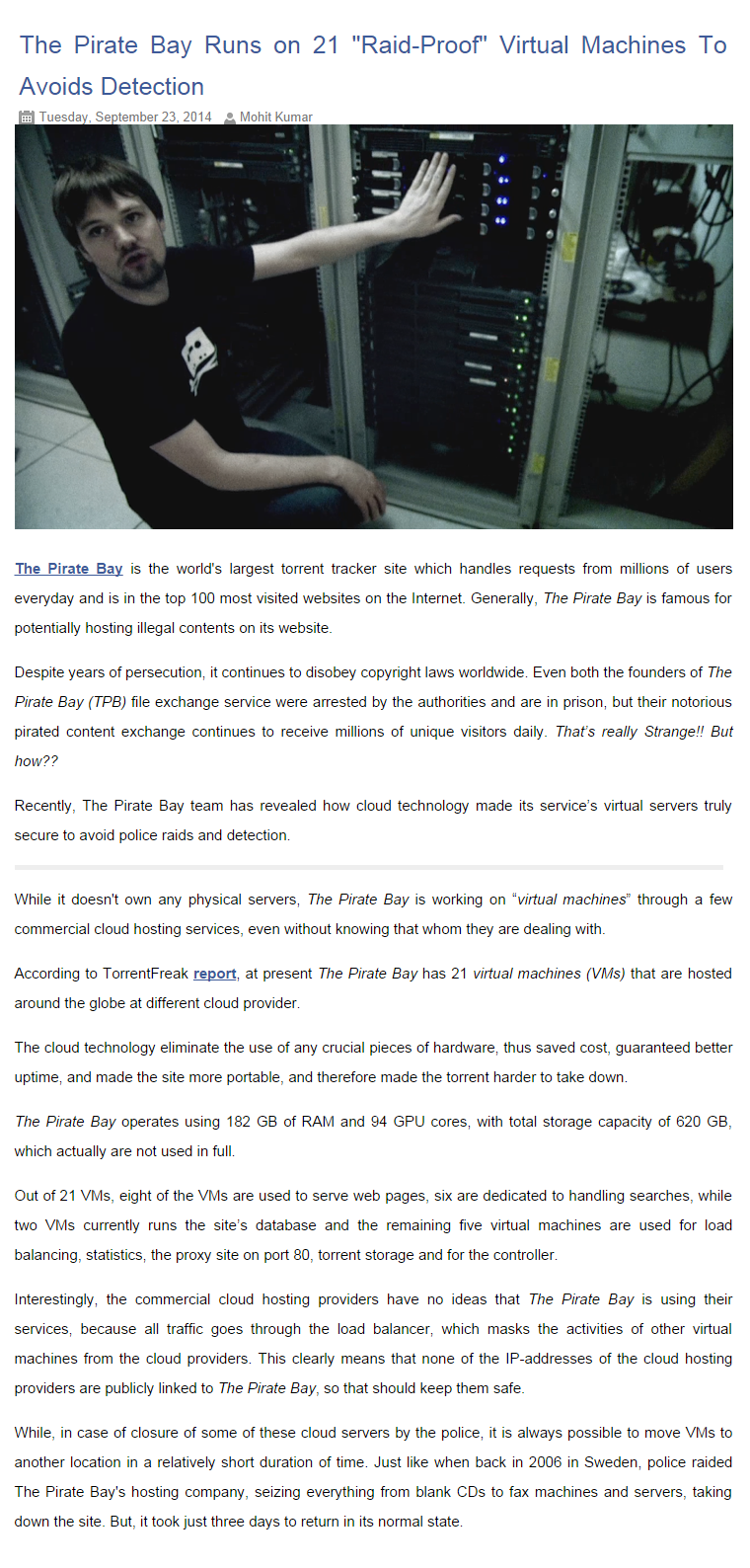
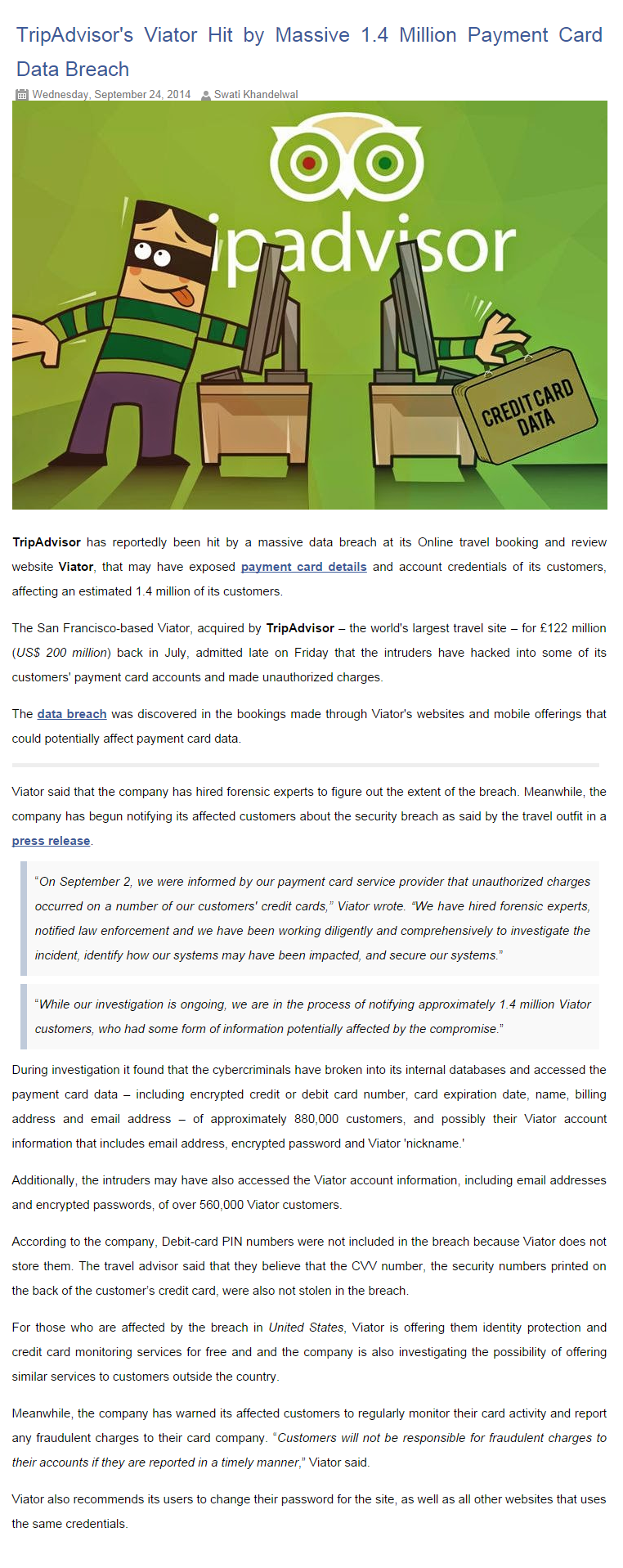
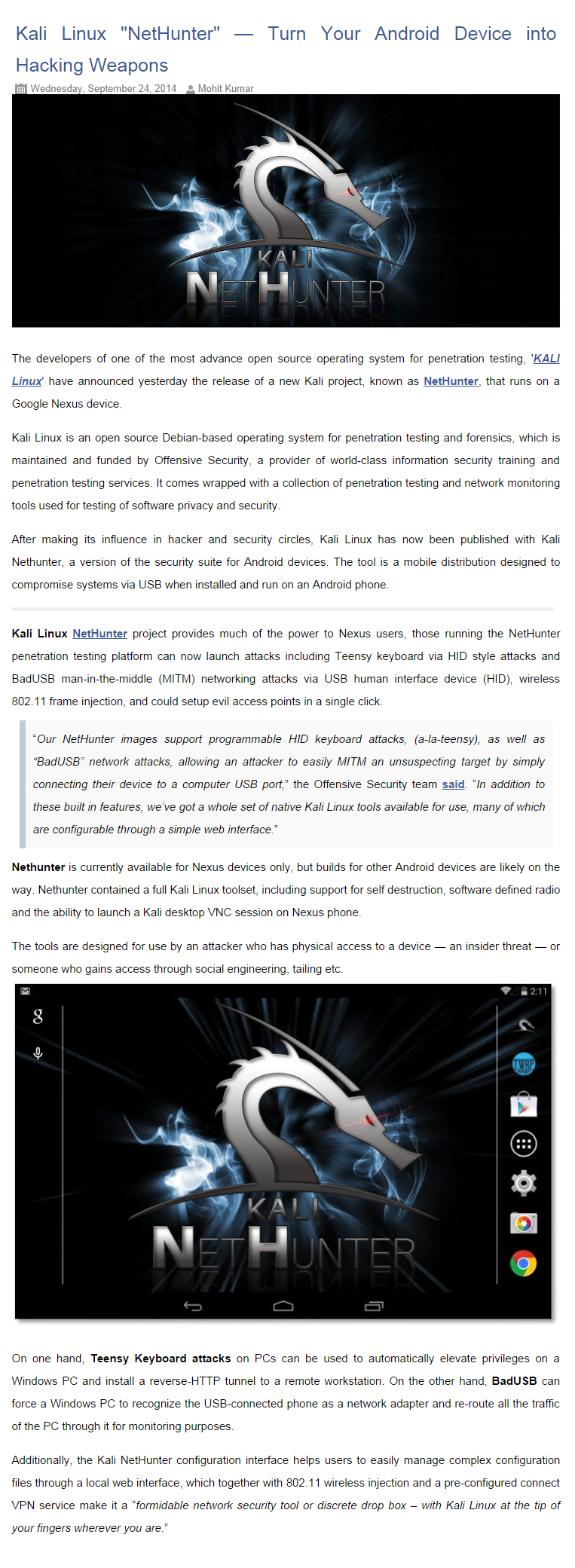
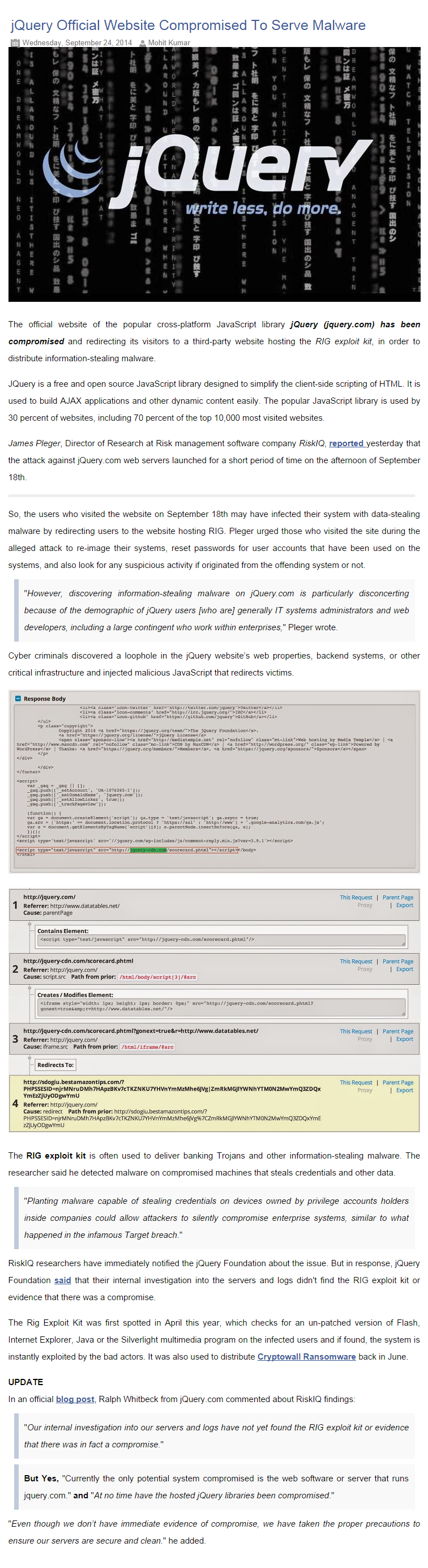
Hacking 101
- Thread starter General Grievous
- Start date
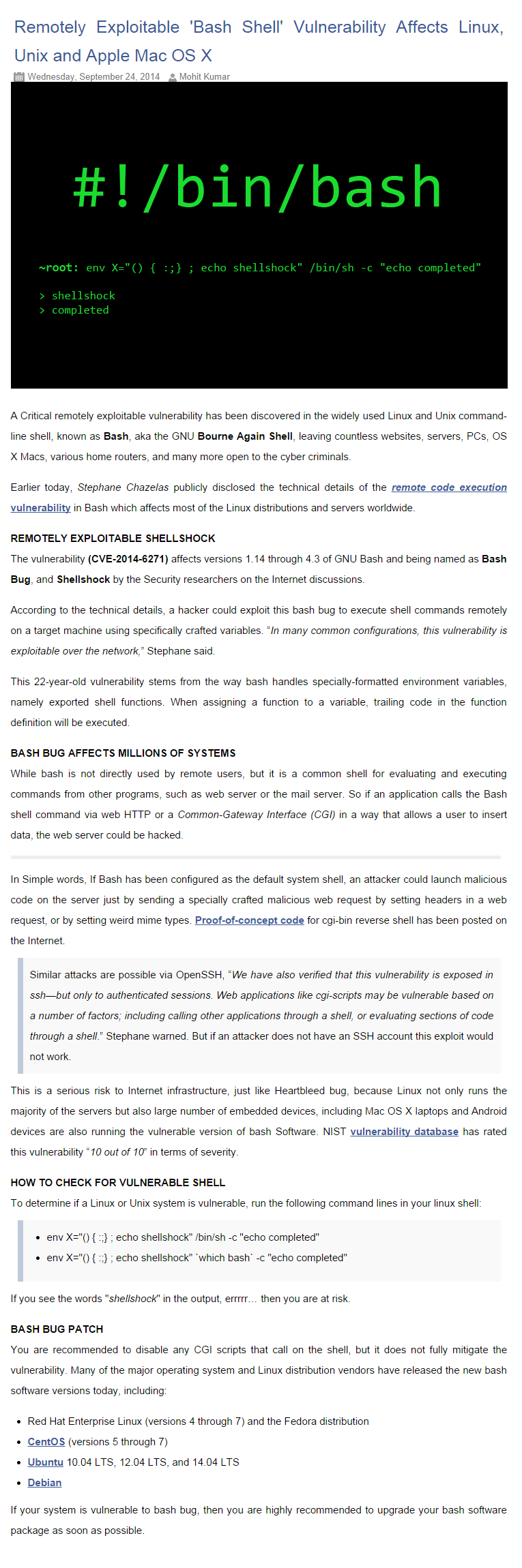
StealthGenie 'stalker app' maker arrested over its alleged privacy violation
First-of-its-kind prosecution argues StealthGenie violates personal privacy
PUBLISHED : Wednesday, 01 October, 2014, 3:58am
UPDATED : Wednesday, 01 October, 2014, 3:58am
The Washington Post
StealthGenie can secretly monitor phone calls and other personal communications
US federal officials have announced the arrest of the maker of a smartphone app marketed as a tool for catching cheating spouses by eavesdropping on their calls and tracking their locations, a system that critics have dubbed "stalker apps".
In the first prosecution of its kind, officials said that the StealthGenie violated the law by offering the ability to secretly monitor phone calls and other personal communications, something typically legal only for law enforcement.
Activists working to prevent domestic violence have long urged United States officials to take more aggressive action on the hi-tech tools used by abusers.
Although it often was advertised as a system for monitoring small children or suspicious employees, surveillance software frequently ended up in the hands of people who might beat partners, activists said.
StealthGenie, with prices ranging from US$100 to US$200 a year, allows buyers to track nearly any movement or utterance of their target, underscoring the remarkable surveillance capabilities of iPhones, BlackBerrys and Android devices.
"The fact that it is running in surreptitious mode is what makes it so foul," said Cindy Southworth of the National Network to End Domestic Violence. "They work really hard to make it totally secretive."
The chief executive of the company making StealthGenie, Hammad Akbar, 31, of Lahore, Pakistan, was arrested in Los Angeles on Saturday, according to the Justice Department.
A grand jury in the Eastern District of Virginia indicted Akbar in August, and the case involves charges of conspiracy, sale of a surreptitious interception device and advertising a surreptitious interception device.
That previously sealed indictment was announced on Monday afternoon.
Court filings suggest that Akbar has contended that any legal issues were limited to the users of StealthGenie, not its maker.
"When the customer buys the product, they assume all responsibility," he wrote in a 2011 email, court filings show. "We do not need to describe the legal issues."
Efforts to reach Akbar's lawyer, based in Los Angeles, were not successful.
"Selling spyware is not just reprehensible, it's a crime," assistant Attorney General Leslie Caldwell, head of the Justice Department's criminal division, said.
"Apps like StealthGenie are expressly designed for use by stalkers and domestic abusers who want to know every detail of a victim's personal life, all without the victim's knowledge.
"The criminal division is committed to cracking down on those who seek to profit from technology designed and used to commit brazen invasions of individual privacy."
'Anonymous' hacker group declares cyber war on Hong Kong government, police
Citing mistreatment against Occupy Central protesters, the self-styled 'hacktivist' group threatens to disrupt Hong Kong government websites
PUBLISHED : Thursday, 02 October, 2014, 11:36am
UPDATED : Thursday, 02 October, 2014, 12:11pm
Jeremy Blum [email protected]

The Anonymous hacker logo laid on top of footage from the Occupy Central protests. Photo: SCMP Pictures
Hacker group Anonymous has declared war on the Hong Kong government and hacked into a number of Hong Kong websites, citing the treatment of protesters during Occupy Central as the main impetus for the attack.
In a video sent to American news portal News2share on Wednesday, Anonymous compares the tear gas and pepper spray used by Hong Kong riot police on Occupy Central protesters to American police tactics used in Ferguson, Missouri earlier this year.
The group also threatens to disclose personal information and deface multiple Hong Kong websites over the coming days. Due to the nebulous nature of Anonymous, it is almost impossible to verify the extent of the attacks and the locations and identities of the hackers behind them.
Watch: Anonymous declares cyber warfare on Hong Kong (via News2share)
<iframe src="//www.youtube.com/embed/BFO0hN9Ptdc?rel=0&controls=0&showinfo=0" allowfullscreen="" height="360" width="640" frameborder="0"></iframe>
The full transcript of the video is as follows:
Greetings, world. We are Anonymous.
It has come to our attention that recent tactics used against peaceful protesters here in the United States have found their way to Hong Kong. To the protesters in Hong Kong, we have heard your plea for help. Take heart and take to your streets. You are not alone in this fight. Anonymous members all over the world stand with you, and will help in your fight for democracy.
To the Hong Kong police and any others that are called to the protests, we are watching you very closely and have already begun to wage war on you for your inhumane actions against your own citizens. If you continue to abuse, harass or harm protesters, we will continue to deface and take every web-based asset of your government off line. That Is not a threat. It is a promise.
Attacking protesters will result in releasing personal information of all of your government officials. We will seize all your databases and e-mail pools and dump them on the Internet. This is your first and only warning. The time has come for democracy for the citizens of Hong Kong. The line has been drawn in the sand. The police are to protect, not trample on, the freedoms and democracy of their citizens. Until justice prevails, hack and protest will replace it. The cause of security and democracy will be grounds for the assault on your virtual infrastructure. Take this opportunity to stand down while we give it to you, or it will get a lot worse.
Operation Hong Kong engaged. We are Anonymous. We are legion. We do not forgive. We do not forget. Government of Hong Kong, expect us.
One of the sites hacked by Anonymous. Photo: SCMP Pictures
A quick look at the websites hacked by Anonymous shows garbled homepages complete with blaring music, pictures of the group’s logo and a block of text which reads: “We Are Sick And Tired Of your Bullsh*t! This is Operation HongKong. We Will Not Stop. We Will Not Give Up! Youve Pissed All The Anons Off #SaveHongKong #OpHongKong #Anonymous# #Hacked”
Despite these vehement threats, the hacks thus far appear to be not on government websites but rather small organisations - including an Autism Partnership site - registered with a .hk domain name.

An Autism Partnership site hacked by Anonymous. Photo: SCMP Pictures
Ironically, at least one of the sites, owned by Nantong Jiehao Machine Equipment, features simplified Chinese and appears to be based in mainland China, despite the .hk registration.
News of Anonymous’ hack attack has been slowly spreading on Twitter, with several accounts associated with the group either tweeting messages related to Hong Kong or spreading news of the attack via the #OpHK hashtag.
____________________________________
Anonymous, which considers itself an international network of “hacktivists”, has become well known for hijacking government and business websites and unleashing distributed denial-of-service (DDoS) attacks – where sites are continuously bombarded with traffic until their servers overload.
In the past, Anonymous has achieved renown for hacking businesses including Visa and Sony, as well as government websites in the US, Singapore, and Israel. The group has publicly announced its support of freedom of speech, and has endorsed WikiLeaks on multiple occasions.
Hackers who attacked JPMorgan accessed data of 76 million households
JPMorgan says phishing is the main threat, as attackers got access to names and contact details
PUBLISHED : Friday, 03 October, 2014, 8:35pm
UPDATED : Friday, 03 October, 2014, 8:35pm
Bloomberg in Washington and Toronto

JPMorgan has 65 million customers and some of those affected by the incursion were outside the US. Photo: AP
Hackers exploited an employee password to crack a JPMorgan Chase server and pull off one of the largest cyber-attacks ever, accessing data on 76 million households and 7 million businesses.
JPMorgan, the largest US bank, outlined the scope of the breach on Thursday. It reassured clients there was no evidence account numbers and passwords were compromised, even though names and contact data were exposed. People who logged on to certain websites or mobile apps had contact information stolen, the company said.
The bank has been struggling to head off damage since the incident was first reported in August. New details of how attackers accomplished the feat over months, including their initial entry, were provided by two people briefed on the investigation. JPMorgan said the threat now was phishing, in which criminals try to trick people into handing over more valuable data, such as user IDs and passwords.
"If they find the CEO of a company, they know this person's worth a lot; they would try to attack that person," said Jeff Tjiputra, cybersecurity programme chairman at the University of Maryland University College.
In addition to contact information, hackers tapped data identifying whether customers were clients of the private bank, mortgage, auto or credit card divisions, said Patricia Wexler, a JPMorgan spokeswoman.
"There's no evidence that account information - things like account numbers, passwords, log-in IDs - were accessed, viewed or acquired," Wexler said. For example, she said, the hackers wouldn't know the balance of a customer's mortgage, only that they were a client of that unit.
JPMorgan has 65 million customers and some of those affected by the incursion were outside the US, she said. Information on both current and former customers was exposed, as well as on non-customers, including people who may have logged on to JPMorgan websites to conduct transactions with bank clients.
Data was compromised through Chase.com and JPMorganOnline.com and the mobile apps that support those websites, Wexler said.
JPMorgan said customers were not liable for unauthorised transactions that were promptly reported. The company disclosed the scope of the breach in a regulatory filing.
The 76 million households affected compare with the US total of about 115 million as of 2012.
Earlier this year, 145 million personal records were taken in a breach of EBay systems. An attack on retailer Target affected as many as 110 million shoppers. An attack at Home Depot disclosed last month compromised 56 million payment cards.
"The data breach at JPMorgan Chase is yet another example of how Americans' most sensitive personal information is in danger," said US Senator Edward Markey, a Massachusetts Democrat and member of the House of Representatives' commerce committee, who called for legislation to protect against cyberattack.
The incursion at JPMorgan, which is being probed by the FBI, started in June. The hackers entered a web-development server with an employee's user name and password, then wormed their way into the network.
The hackers accessed more than 100 servers that housed data across the spectrum of the company's business, including investment banking, credit cards, and residential banking.
Using sophisticated tools and malicious programs, the intruders siphoned gigabytes of data until the breach was discovered in August. Investigators believe the attack originated in Russia.
Dmitry Peskov, a spokesman for Russian President Vladimir Putin, dismissed the notion that Russia was behind the attack.
FBI Director compares China’s hackers to a ‘drunk burglar’
China's theft of intellectual property through cyberspying is costing American economy billions of dollars every year, says James Comey
PUBLISHED : Monday, 06 October, 2014, 11:11am
UPDATED : Monday, 06 October, 2014, 10:03pm
Agencies in Washington
Most Popular

FBI Director James Comey says China tops the list of countries seeking to pilfer secrets from US firms. Photo: AFP
FBI Director James Comey has compared Chinese hackers to a "drunk burglar" who steals with reckless abandon. He said they cost the US economy billions of dollars every year.
Chinese hackers targeted the intellectual property of US companies in China every day, he said in a television interview.
"I liken them a bit to a drunk burglar. They're kicking in the front door, knocking over the vase, while they're walking out with your television set. They're just prolific. Their strategy seems to be: 'we'll just be everywhere all the time. And there's no way they can stop us'," Comey said on CBS' 60 Minutes.
The US Justice Department earlier this year announced a 31-count indictment against Chinese hackers accused of breaking into computer networks at steel companies and the manufacturers of solar and nuclear technology, with the goal of gaining a competitive advantage. China has denied the allegations.
Comey said China topped the list of countries seeking to pilfer secrets from US firms, suggesting that almost every major firm in America had been targeted.
"There are two kinds of big companies in the United States," he said. "There are those who've been hacked by the Chinese and those who don't know they've been hacked by the Chinese."
Comey cited the historic case of five members of the People's Liberation Army indicted with hacking US companies for trade secrets, a move which outraged China when announced in May.
The case is the first-ever federal prosecution of state actors over cyber-espionage.
The PLA unit is accused of hacking into US computers to benefit Chinese state-owned companies, leading to job losses in the United States in steel, solar and other industries.
"They are extremely aggressive and widespread in their efforts to break into American systems to steal information that would benefit their industry," Comey said of China's hackers.
Comey said China was seeking to obtain "information that's useful to them so they don't have to invent"
"They can copy or steal to learn about how a company might approach negotiations with a Chinese company, all manner of things," he said.
Asked for a dollar estimate of the intellectual property stolen by China, Comey said it was incalculable. "Impossible to count," he said. Billions."
Last week, big bank JPMorgan Chase revealed that a hack it had reported in August had compromised data on 76 million household customers and seven million businesses, including their names, email addresses and telephone numbers.
Treasury Secretary Jack Lew, speaking on ABC television, declined to address the JPMorgan Chase case specifically. But he stressed: "We have made enormous efforts to bring attention to this and resources to this. The president [Barack Obama] has taken action through an executive order.
"Look, we have a lot of concerns about the sources of attacks because there are many different sources. "
FBI Director James Comey has compared Chinese hackers to a "drunk burglar" who steals with reckless abandon. He said they cost the US economy billions of dollars every year.
Chinese hackers targeted the intellectual property of US companies in China every day, he said in a television interview.
"I liken them a bit to a drunk burglar. They're kicking in the front door, knocking over the vase, while they're walking out with your television set. They're just prolific. Their strategy seems to be: 'we'll just be everywhere all the time. And there's no way they can stop us'," Comey said on CBS' 60 Minutes.
The US Justice Department earlier this year announced a 31-count indictment against Chinese hackers accused of breaking into computer networks at steel companies and the manufacturers of solar and nuclear technology, with the goal of gaining a competitive advantage. China has denied the allegations.
Comey said China topped the list of countries seeking to pilfer secrets from US firms, suggesting that almost every major firm in America had been targeted.
"There are two kinds of big companies in the United States," he said. "There are those who've been hacked by the Chinese and those who don't know they've been hacked by the Chinese."
Comey cited the historic case of five members of the People's Liberation Army indicted with hacking US companies for trade secrets, a move which outraged China when announced in May.
The case is the first-ever federal prosecution of state actors over cyber-espionage.
The PLA unit is accused of hacking into US computers to benefit Chinese state-owned companies, leading to job losses in the United States in steel, solar and other industries.
"They are extremely aggressive and widespread in their efforts to break into American systems to steal information that would benefit their industry," Comey said of China's hackers.
Comey said China was seeking to obtain "information that's useful to them so they don't have to invent"
"They can copy or steal to learn about how a company might approach negotiations with a Chinese company, all manner of things," he said.
Asked for a dollar estimate of the intellectual property stolen by China, Comey said it was incalculable. "Impossible to count," he said. Billions."
Last week, big bank JPMorgan Chase revealed that a hack it had reported in August had compromised data on 76 million household customers and seven million businesses, including their names, email addresses and telephone numbers.
Treasury Secretary Jack Lew, speaking on ABC television, declined to address the JPMorgan Chase case specifically. But he stressed: "We have made enormous efforts to bring attention to this and resources to this. The president [Barack Obama] has taken action through an executive order.
"Look, we have a lot of concerns about the sources of attacks because there are many different sources. "
Associated Press, Agence France-Presse
US companies considering 'hacking back' as cyber warfare intensifies
Tiring of having little option but to tolerate cyber attacks, firms are increasingly looking at going on the offensive and 'hacking back'
PUBLISHED : Friday, 10 October, 2014, 8:42pm
UPDATED : Friday, 10 October, 2014, 8:42pm
The Washington Post

Yet the idea of hacking back, some prefer the more genteel-sounding "active defence", has gained currency as frustration grows about the inability of government to stem lawlessness in cyberspace, experts say.
The recent rash of cyberattacks on leading US companies has highlighted the scant options available to the victims, who often can do little more than endure the bad publicity and harden their defences in hopes of thwarting the next assault.
But behind the scenes, talk among company officials increasingly turns to an idea once considered so reckless that few would admit to even considering it, which was going on the offensive, or "hacking back".
The mere mention of it within cybersecurity circles can prompt a lecture about the many risks, starting with the fact that most forms of hacking back are illegal and ending with warnings that retaliating could spark full-scale cyberwar, with collateral damage across the internet.
Yet the idea of hacking back, some prefer the more genteel-sounding "active defence", has gained currency as frustration grows about the inability of government to stem lawlessness in cyberspace, experts say.
The list of possible counter measures also has grown more refined, less about punishing attackers than keeping them from profiting from their crimes.
"Active defence is happening. It's not mainstream. It's very selective," said Tom Kellermann, chief cybersecurity officer for Trend Micro and a former member of President Barack Obama's commission on cybersecurity.
He added that he and his company would never do it: "For you to hack back, you actually put at risk innocents."
One vocal advocate of some limited forms of hacking back, former National Security Agency lawyer Stewart Baker, said even some government officials were warming to the idea.
He said officials were more likely to consider assisting frustrated companies than threaten prosecution when they talked about going on the offensive.
"The government is giving ground silently and bit by bit on this by being more open," said Baker, now a partner at Steptoe & Johnson. "I have a strong sense from everything I've heard … that they're much more willing to help companies that want to do this."
A popular metaphor in these discussions has been the exploding dye pack that bank tellers sometimes slip into bags of cash during old-fashioned bank robberies.
The cyberspace equivalent, called a "beacon", potentially could be attached to sensitive data, making it easier to spot both the stolen loot and determine who spirited it away across the internet.
Other ideas include tricking hackers into stealing a fake set of sensitive data, then tracking its movements across cyberspace.
Some experts also suggest taking advantage of the way hackers often operate, moving files in stages from a victim's network to a remote server before collecting them hours later.
The time lag potentially gives companies time to spot the stolen files and destroy them before hackers can complete the theft.
Hacking back is a staple of conversations at cybersecurity conferences.
At the Black Hat USA security conference in 2012, 36 per cent of respondents said they had engaged in "retaliatory hacking" on at least one occasion, according to cybersecurity company nCircle, which conducted the survey of 181 conference attendees.
Financial industry security experts have had private discussions about the possibility of retaliatory cyberattacks but concluded the legal risks were too great to pursue the idea, according to technology sources who were not authorised to speak publicly.
"Most of the offensive talk is from the private sector, saying, 'I've had enough and I'm going to go do something about it'," said Republican congressman Mike Rogers, chairman of the House intelligence committee, at a cybersecurity summit at The Washing ton Post last week.
Yet Rogers, like many other government officials, has publicly warned about the dangers of hacking back.
Entering another person or company's network without permission violates the Computer Fraud and Abuse Act, officials say, even if the intrusion happens in the course of attempting to identify hackers or destroy data they have stolen.
Any resulting consequences, even unintended ones, such as accidentally damaging an innocent company's network, could cause significant legal liability. Plus, it's notoriously difficult to correctly identify who is behind a cyberattack.
"Attribution is very difficult to do," said White House cybersecurity coordinator Michael Daniel. "The bad guys don't tend to use things labelled 'bad guy server'.
They tend to corrupt and use innocent third-party infrastructure. So we have always said you need to be really cautious about taking activities that are ' hacking back' or even what some people try to call 'active defence'."
Russian held in US faces more credit card data hacking charges
PUBLISHED : Friday, 10 October, 2014, 8:59pm
UPDATED : Friday, 10 October, 2014, 8:59pm
Agence France-Presse in Washington

Roman Seleznev
A Russian national arrested this year by US officials has been indicted on additional hacking charges, alleging he led a scheme to steal some two million credit card numbers.
Roman Seleznev, the son of a Russian lawmaker, now faces 40 criminal counts including wire fraud and identity theft, the US Justice Department said.
The superseding indictment returned by a grand jury in Seattle offered more details on the alleged scheme to create an underground network to facilitate the theft and sales of credit card data.
Seleznev, 30, was arrested in July, to face charges in a prior indictment. He and his partners hacked into computer payment systems and stole credit card numbers from dozens of retailers in Seattle and other cities around the United States, prosecutors alleged.
The numbers were then sold on "dump shop websites" which facilitate sales of stolen credit card information.
"The additions in this superseding indictment show how cybercriminals use the internet not only to infiltrate and steal sensitive data, but also to teach other criminals how to navigate the credit card selling underworld and get equipment that can be used to defraud US citizens," said Assistant Attorney General Leslie Caldwell.
Seleznev is currently scheduled for trial on November 3 and will be arraigned on the new charges next week.
In July, Moscow accused Washington of abducting Seleznev from the Maldives. The US insisted there was "no kidnapping involved" in the arrest.
Snapchat blames photo leaks on third-party apps
PUBLISHED : Sunday, 12 October, 2014, 6:38am
UPDATED : Sunday, 12 October, 2014, 6:38am
Reuters in San Francisco

Snapchat blames photo leaks on third-party apps
Mobile messaging company Snapchat has blamed third-party software apps for security lapses that have put its users' private photos at risk of online publication by hackers.
A file containing at least 100,000 Snapchat photos had been collected by hackers who were preparing to publish them online, according to a report on the Business Insider blog. Snapchat lets users send photos and videos that disappear in seconds.
"We can confirm that Snapchat servers were never breached and were not the source of these leaks," the company said.
Users were "allegedly victimised by their use of third-party apps to send and receive snaps, a practice that we expressly prohibit in our terms of use precisely because they compromise our users' security".
Snapchat, one of a crop of new apps that compete with Twitter and Facebook, is popular among teenagers. Some media reports raised concerns that the hackers' file could contain nude "selfie" pictures of teens who expected the photos to be deleted.
Leaked photos could also become problematic for Snapchat, which has faced criticism over privacy practices. It is now raising money in a funding round that would give it a US$10 billion valuation, according to reports.
According to Business Insider, hackers may have obtained the photos by breaching third-party services that allow consumers to save the Snapchat photos they receive. Users of the online forum 4Chan downloaded the files and were creating a searchable database of the stolen photos, the report said.
Tal Klein, a vice president at cloud security firm Adallom, said he could not rule out the possibility that the incident was a hoax.
He noted some of the purported Snapchat photos posted on 4Chan had digital signatures that matched his firm's database of stolen images previously circulated online. That suggested the episode could be fictitious, or that the supposed cache of new photos was a collection of previously stolen Snapchat images aggregated by hackers, said Klein.
The development comes after nude pictures of Jennifer Lawrence and dozens of other actresses were posted on 4Chan.
______________________________________________
Hackers access payment cards of Kmart customers
Sears Holdings said hackers have stolen the details of some customer payment cards at its Kmart stores, the latest in a series of computer security breaches to hit US companies.
The US Secret Service confirmed it was investigating the breach, which occurred in September and compromised the systems of Kmart, which has about 1,200 stores across the United States. The breach did not affect the Sears department store chain.
A Sears spokesman said he could not say how many credit and debit card numbers had been taken.
The spokesman added that the personal information, debit card PINs, email addresses and social security numbers of its customers remained safe.
Security professionals said they were not surprised to learn that yet another major retailer was reporting a breach, adding they believed many big merchants did not have adequate systems for detecting cyberattacks.
Chinese government websites attacked after Anonymous vow to support HK protests
Information from two government affiliated websites in Zhejiang province hacked, activists claim
PUBLISHED : Sunday, 12 October, 2014, 3:56pm
UPDATED : Sunday, 12 October, 2014, 5:13pm
Chris Luo

A person claiming to speak for activist hacker group Anonymous seen threatening Singapore in video released last year. Photo: AFP
The Anonymous group of computer hackers released hundreds of Chinese phone numbers and email addresses on Sunday morning shortly after the government denounced its threat of cyberattacks in apparent support of Hong Kong’s democracy movement.
The international hacker group released approximately 600 entries of contact information from China’s Zhejiang province in a message released early on Sunday morning.
Some of the entries show individual IP addresses and email addresses, while others carry names and mobile phone numbers.
With the release the group followed up on its threat from Friday to release data from Chinese government websites.
The targets of the latest attacks were the website of the Ningbo Free Trade Zone in Zhejiang province and a job search site run by the Changxing county administration, also in the coastal province.
It was not immediately clear why these two websites had been targeted. The government offices in charge of the two websites could not be reached on Sunday. China's Ministry of National Defense and Ministry of Foreign Affairs are also not immediately available to comment.
To a large extent, the contact information revealed by Anonymous belonged to small local businesses searching for talent in Zhejiang.
Much of the information was already publicly available online.
Anonymous claimed it had already infiltrated more than 50 Chinese government databases and leaked 50,000 usernames and emails, saying it was fullfilling promises to “stand and fight alongside the citizens of Hong Kong”.
The group had earlier targeted websites in Hong Kong after issuing a first warning on October 2. In a public video message, Anonymous declared cyberwar on Hong Kong’s government and police force as punishment for the use of tear gas against demonstrators, and pledged to help Hongkonger’s struggle for democracy.
It threatened to hack into government databases and release personal information of government officials.
Anonymous made some sites either inaccessible or intermittently accessible on October 3.
The websites of the Silent Majority for Hong Kong, and the Democratic Alliance for the Betterment and Progress of Hong Kong, Chief Secretary for Administration Carrie Lam Cheng Yuet-ngor, Hong Kong police, the Occupy Central civil disobedience movement, Ocean Park and the Hong Kong International Airport were targed at the time.
Michael Gazeley, managing director at security service provider Network Box, said it is difficult to “make a judgment whether [the earlier attacks] really are [the work] of Anonymous to start with” because Anonymous is a loosely associated group of hackers.
“It almost seems that there are some hackers that are trying to attack the government and other hackers trying to attack the Occupy Central website,” Gazeley said, referring to the first wave of attacks Anonymous claimed on Hong Kong websites.
"You can’t really be sure which actions are really [that of] Anonymous, or somebody claiming to be Anonymous, and if they can be definitely attributed to Anonymous.”
Gazeley added that the “Chinese government has got a lot of cyber security in place" as "they take security very seriously”, but it is difficult to assess what it would do in particular to respond to the potential attacks.
Cyberworld's wild west: black hats vs. white hats
Chang Kuo-wei and Staff Reporter
2014-10-12
A still from the film "Transcendence." (File photo courtesy of Alcon Entertainment)
Cyberworld in China is dominated by two types of hackers, the black hats who represent the evil, and the white hats who represent good. The terms are derived from old Western movies where the good guys wore white hats and the bad guys wore black ones.
A black hat hacker is a person who attempts to find vulnerabilities in computer security systems and exploit them for personal financial gain or other malevolent reasons. This sets them apart from white hat hackers, who are security specialists employed to use hacking methods for finding security flaws that could be exploited by black hats.
According to Guangzhou's the Southern Weekend, on Sept. 12 at a forum on cybersecurity held by Wooyun, a third-party platform for reporting security bugs, a white hat said that there are three types of hacking victims-those whose accounts have been hacked, those unaware of having been hacked, and those reluctant to admit that they have been hacked.
"Oh, there is another type-those who are being hacked," he added jokingly.
Chinese computers hackers have caused sporadic chaos since they emerged in 1990. In 1998, when anti-Chinese riots broke out in Indonesia, they launched their first massive cyberattack. The attack, which was deemed patriotic then, was to spam the Indonesian government's accounts.
Now, the original idealism of Chinese hacking has been tainted by money, and an industry has emerged where black hats trade information for economic gains.
"Currently, the highest daily income of a black hat is 10,000 yuan (US$1,631), which is equivalent to the highest monthly income of a white hat," founder of Wooyun, Fang Xiaodun, noted.
Attacks are usually launched through intrusive websites that spread Trojan Horse viruses which wreak havoc on computer systems or networks and steal valuable information, including e-mail account details and customer data held by companies, for sale or extortion to mak profits.
Just like the wild west, the process of setting up and tearing down firewalls that protect computer systems or networks has turned into a veritable shootout between white hats and black hats.
Besides these two types, there are also those known as grey hat hackers. A grey hat is someone who lies midway between the black and white concepts. They may use their skills for legal or illegal purposes, but not for personal gains. Grey hats only use their skills to prove that they can accomplish a feat, not to make money off it. Once they cross that line, they have entered black hat territory.
Similar threads
- Replies
- 3
- Views
- 299
- Replies
- 10
- Views
- 708
- Replies
- 69
- Views
- 3K