-
IP addresses are NOT logged in this forum so there's no point asking. Please note that this forum is full of homophobes, racists, lunatics, schizophrenics & absolute nut jobs with a smattering of geniuses, Chinese chauvinists, Moderate Muslims and last but not least a couple of "know-it-alls" constantly sprouting their dubious wisdom. If you believe that content generated by unsavory characters might cause you offense PLEASE LEAVE NOW! Sammyboy Admin and Staff are not responsible for your hurt feelings should you choose to read any of the content here. The OTHER forum is HERE so please stop asking.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
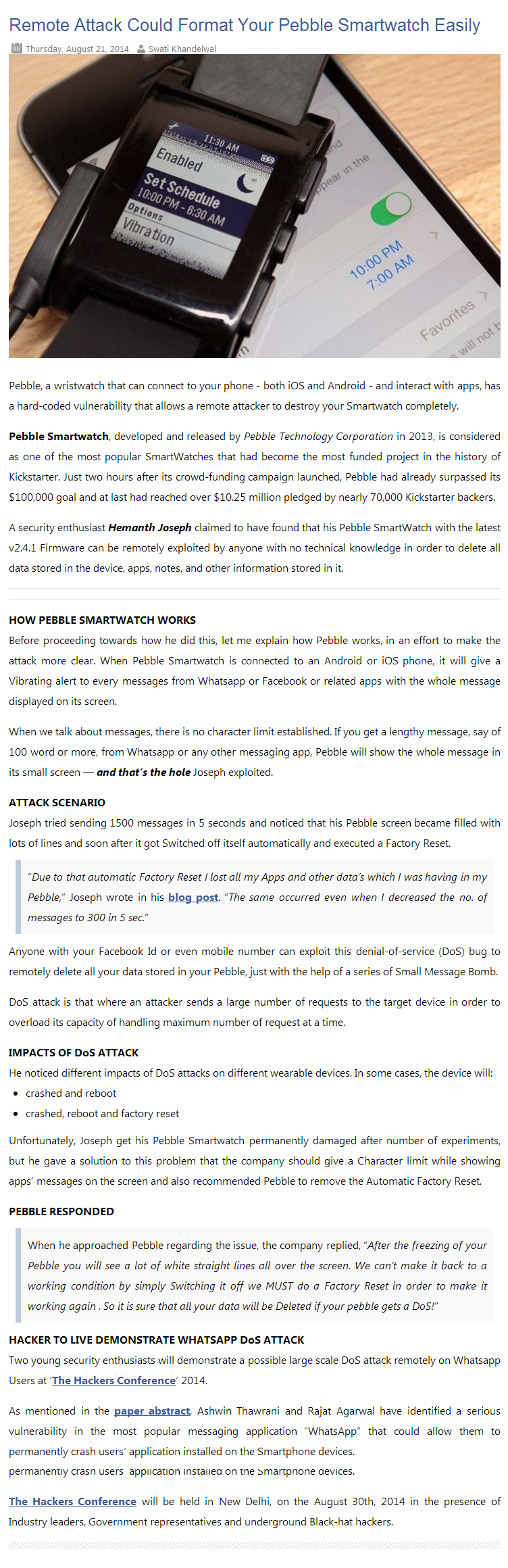
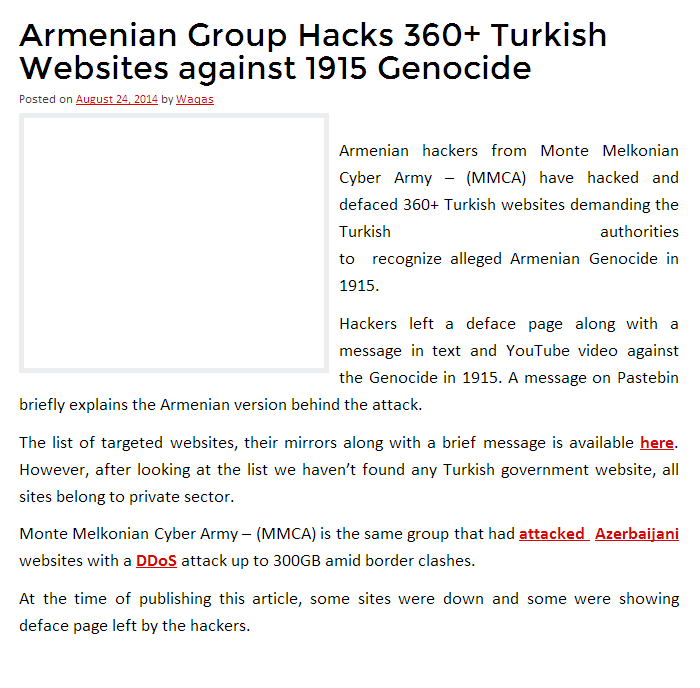
Hacking 101
- Thread starter General Grievous
- Start date
good info buddy. Ups you.
Worst hackers, looters and stalkers are the search engine themselves.
What nice name robot crawler to that help you to move up the search engine ladder.
Now they even illegally copy your img source and post it on their web sight.
These search engines, Google the main culprit, are private limited company getting more law suits soon. Class actions law suit are common, initiated by unemployed law students, to take on Google the private ltd company. Facebook is also going to kenna the same.
Archive? what is archive of your htmls, image has to do with search engine business. Go archive your own google company biz, and stop noosing at private html file.
These days better to have password protected site (use .php) that least least make hackers work harder to crack your site than let google suka suka scoop your html file and hack you (first line of hack).
Who give pte ltd companies search engine biz permission to hack your html file?
<meta name="robots" content="noindex,nofollow,noarchive">
<meta name="robots" content="none">
<meta name="googlebot" content="noindex,nofollow,noarchive">
Need to plant new codes to trace back hackers IP address and location and hack back their PCs. Most hackers use their own PC anyway and easily trace back.
Worst hackers, looters and stalkers are the search engine themselves.
What nice name robot crawler to that help you to move up the search engine ladder.
Now they even illegally copy your img source and post it on their web sight.
These search engines, Google the main culprit, are private limited company getting more law suits soon. Class actions law suit are common, initiated by unemployed law students, to take on Google the private ltd company. Facebook is also going to kenna the same.
Archive? what is archive of your htmls, image has to do with search engine business. Go archive your own google company biz, and stop noosing at private html file.
These days better to have password protected site (use .php) that least least make hackers work harder to crack your site than let google suka suka scoop your html file and hack you (first line of hack).
Who give pte ltd companies search engine biz permission to hack your html file?
<meta name="robots" content="noindex,nofollow,noarchive">
<meta name="robots" content="none">
<meta name="googlebot" content="noindex,nofollow,noarchive">
Need to plant new codes to trace back hackers IP address and location and hack back their PCs. Most hackers use their own PC anyway and easily trace back.
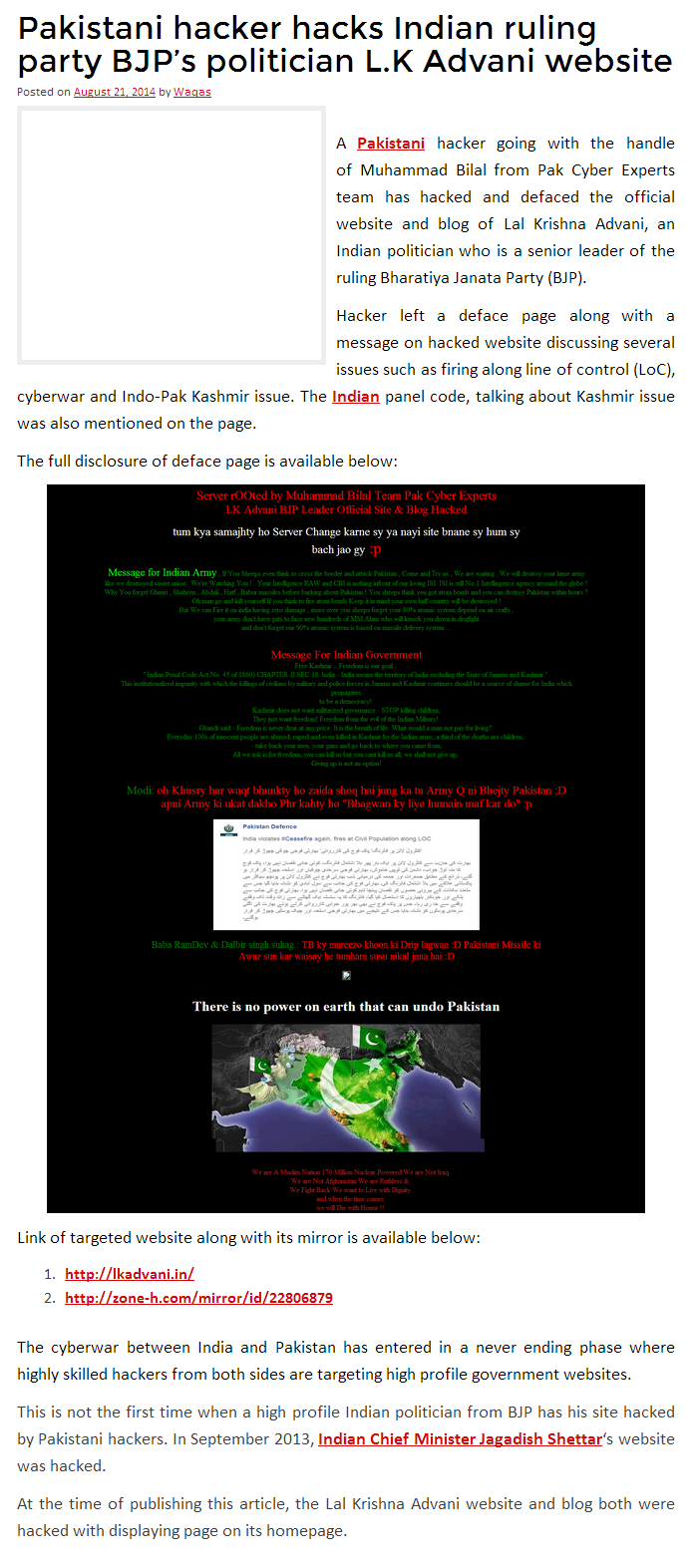
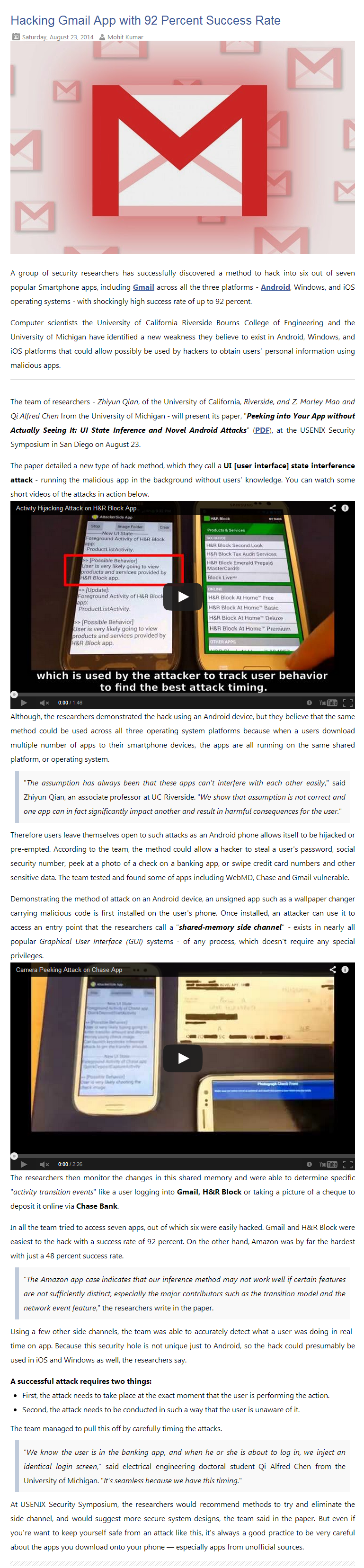
Chinese hacker targeted US military contractors, Senate panel committee finds
Senate committee claims attacks gained insight into logistics and 'foothold' to disrupt operations
PUBLISHED : Thursday, 18 September, 2014, 4:59am
UPDATED : Thursday, 18 September, 2014, 9:51am
Reuters in Washington

Senate Armed Services Committee chairman Senator Carl Levin talks to media about cyberattacks from China. Photo: AP
Hackers associated with the Chinese government have repeatedly infiltrated the computer systems of US airlines, technology companies and other contractors involved in the movement of US troops and military equipment, a US Senate panel has found.
The Senate Armed Services Committee’s year-long probe, concluded in March but made public on Wednesday, found the military’s US Transportation Command, or Transcom, was aware of only two out of at least 20 such cyber intrusions within a single year.
The investigation also found gaps in reporting requirements and a lack of information sharing among US government entities. That in turn left the US military largely unaware of computer compromises of its contractors.
“These peacetime intrusions into the networks of key defence contractors are more evidence of China’s aggressive actions in cyberspace,” Democratic Senator Carl Levin of Michigan, the committee’s chairman, said in releasing the report.
Officials with the Chinese Embassy in Washington did not immediately comment.
Cybersecurity expert Dmitri Alperovitch, chief technology officer with the security firm Crowdstrike, said China had for years shown a keen interest in the logistical patterns of the US military.
The investigation focused on the US military’s ability to seamlessly tap civilian air, shipping and other transportation assets for tasks including troop deployments and the timely arrival of supplies from food to ammunition to fuel.
Those companies typically do not have the same level of defence against hackers as major weapons-makers or the military itself.
“The military uses secret or top-secret networks that are not on the internet, but private companies do not,” said Alperovitch. “That’s a real challenge.”
The FBI said in a statement that it “continues to aggressively investigate cyber intrusions emanating from state-sponsored actors and other criminals.
“We remain committed to working with our interagency partners to identify threats, protect the nation’s infrastructure from potential harm, and hold accountable those groups and individuals that pose a threat in cyberspace,” the statement added.
In a 12-month period beginning on June 1, 2012, there were about 50 intrusions or other cyber events into the computer networks of Transcom contractors, the 52-page report stated.
At least 20 of those were successful intrusions attributed to an “advanced persistent threat,” a term used to designate sophisticated threats commonly associated with attacks against governments. All of those intrusions were attributed to China.
Senator Jim Inhofe of Oklahoma, the committee’s top Republican, called for a “central clearinghouse” that makes it easy for contractors to report suspicious cyber activity.
“We must ensure that cyber intrusions cannot disrupt our mission readiness,” Inhofe said.
The investigation found that a “Chinese military intrusion” into a Transcom contractor between 2008 and 2010 “compromised emails, documents, user passwords and computer code.” In 2012, another intrusion was made into multiple systems of a commercial ship contracted by Transcom, the report said.
The Senate probe could further increase tensions between the two world powers over cyber espionage.
In May US authorities charged five Chinese military officers, accusing them of hacking into American nuclear, metal and solar companies to steal trade secrets.
Last month, Community Health Systems, one of the largest US hospital groups, said Chinese hackers had stolen Social Security numbers and other personal data from some 4.5 million patients.
Similar threads
- Replies
- 3
- Views
- 299
- Replies
- 10
- Views
- 708
- Replies
- 69
- Views
- 3K