https://www.pcworld.com/article/3246204/ces/intel-launches-core-chips-with-amd-radeon-graphics.html
Intel launches five Core chips with Radeon graphics from rival AMD
Intel unveils the speeds, feeds, and prices of the 8th-gen Intel Core with Radeon RX Vega M graphics. The five new chips will appear in notebooks from Dell and HP, plus new Intel NUCs.
Senior Editor, PCWorld | Jan 7, 2018 6:01 PM PT

Intel
More like this
Latest Reviews
Intel’s startling marriage with AMD’s graphics chips has finally borne fruit, as Intel announced five new Core H-series chips that use two variants of the AMD “Vega M” GPU. The combination of Intel and AMD technology should outperform a last-gen system with a discrete Nvidia chip, Intel says.
You can jump straight to our performance section to learn more about Intel’s claims.
The new 8th-generation, quad-core Core i5 and Core i7 chips, together with what AMD calls the Radeon RX Vega M GPU, will power laptops from Dell and HP. They’ll also appear in new Intel-branded “Hades Canyon” NUCs, with prices beginning at $799 and $999, Intel said.
[ Further reading: Our picks for best PC laptops ]
Intel’s announcement Sunday at CES adds a significant amount of detail to the bombshell AMD and Intel dropped in November. Intel’s overarching goal with its Core/Radeon combination has been to deliver a gaming PC with great VR capabilities within an ultrabook form factor. We now know the NUCs will ship in late March, though timing remains unclear for the notebook launches. Intel also shared more information on speeds and feeds.
Intel originally disclosed that its new processor contained an H-series Core chip, the AMD GPU, and HBM2 memory, all within the same package. We now know the clock speeds of the five Core i5 and i7 cores will range from 3.8GHz to 4.2GHz, and that 4GB of HBM2 memory will accompany both the Vega M GH and Vega M GL, the two GPU versions whose 20 and 24 compute units appear to be much more powerful than AMD’s own Ryzen 7 and Ryzen 5 for laptops.
Intel says its new chips will be 7 percent faster in 3DMark versus a Core i7-7700HQ system with an Nvidia GTX 1060 Max-Q (6GB) chip accompanying it, and up to 13 percent faster in games.
Why this matters: For years, we’ve seen integrated notebook processors and notebook chips that use discrete GPUs, each with their own performance tier. Intel’s new partnership with AMD’s Radeon division splits the difference, offering a somewhat modular solution together with graphical performance that’s rather impressive. We all suspected that the Intel-AMD partnership would be a game-changer, and we’re starting to see that it is. We don’t know how Intel will price these chips compared to its more vanilla Core i5 and Core i7 processors, however.
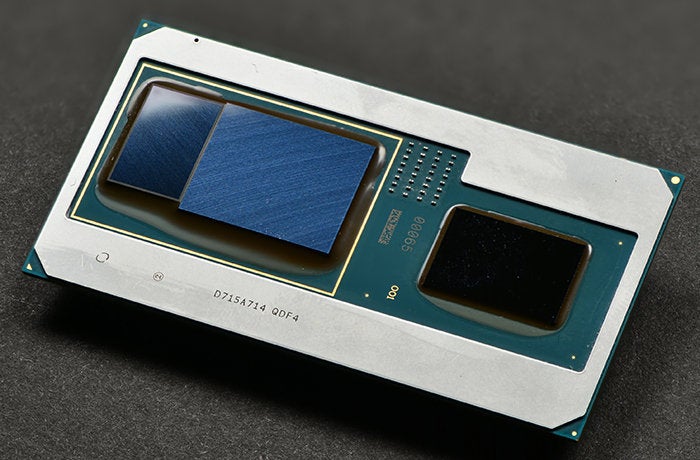 Intel
Intel
Intel’s new 8th-gen Core package with a Vega M core inside of it is surprisingly photogenic.
Table of Contents
What Intel formally refers to as the “8th-gen Intel Core with Radeon RX Vega M graphics” is a typographical nightmare, so it makes more sense to either refer to them with a nickname—whatever it ends up being, Kaby Lake-G perhaps?—or simply by their actual model names. Naturally, since they’re all members of the 8th-gen Core family, all five processors boast four cores and eight processing threads.
Most notable among the new chips—which differ in processor speed, vPro capabilities, and whether they use the Vega M GH and Vega M GL—is the Core i7-8809G. That chip, leaked last week, was the first indication that Intel’s new chips would indeed include AMD’s Vega cores. It’s also the only one of the five chips that totally unlocks the CPU, GPU, and HBM.
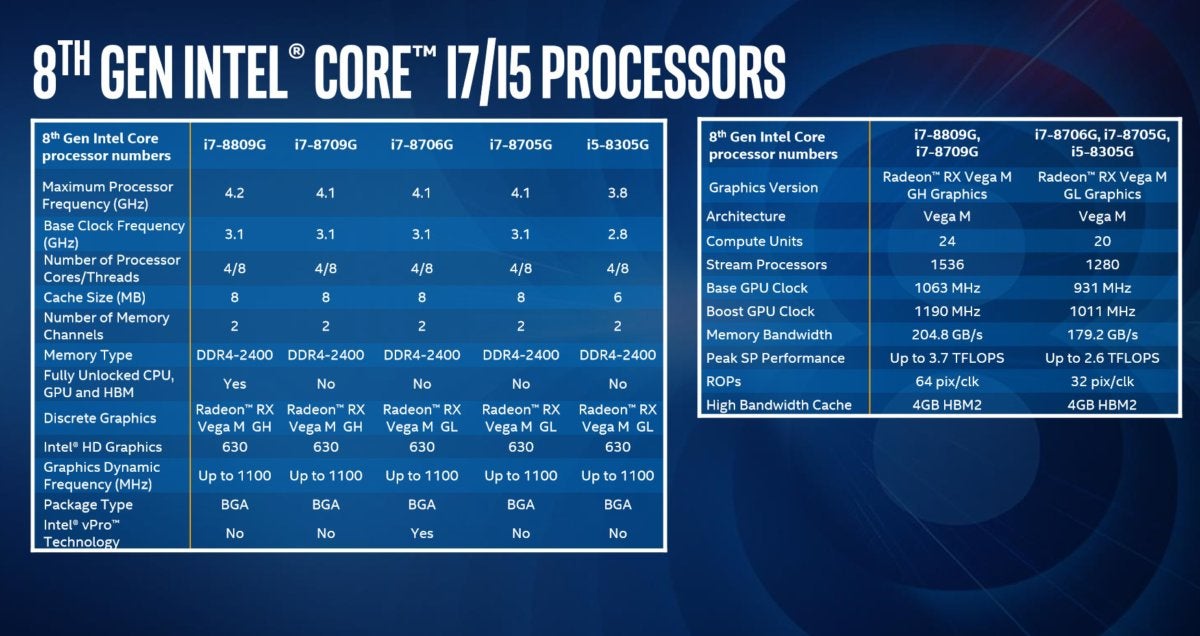
Alongside the Core i7-8809G, though, are the Core i7-8709G, the Core i7-8706G, the 3.1Core i7-8705G, and the Core i5-8305G. As the chart below shows, they all share a common cache size (8MB), a common integrated Intel GPU (the Intel HD620), and two memory channels connecting to DDR4-2400 memory.
Intel
Intel’s five new Intel Core chips with the Radeon RX Vega M core inside. Note that they’re differentiated by clock speed, GPU core, and whether or not they have vPro capabilities. Intel did not disclose prices.
"> Intel
Intel
Intel’s five new Intel Core chips with the Radeon RX Vega M core inside. Note that they’re differentiated by clock speed, GPU core, and whether or not they have vPro capabilities. Intel did not disclose prices.
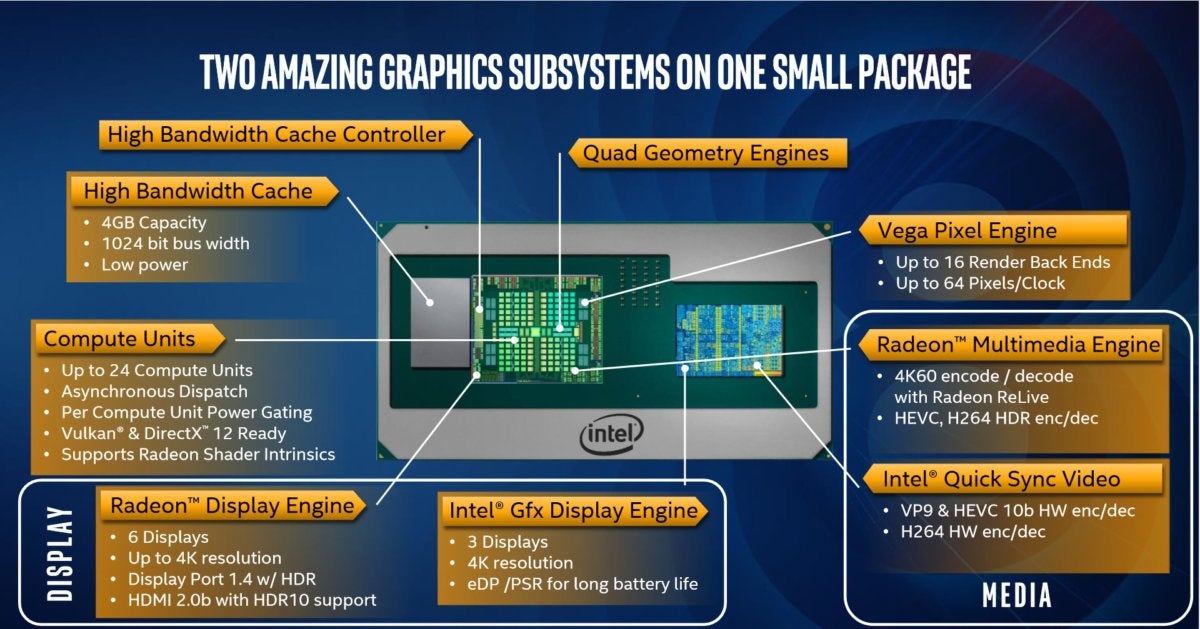
Unfortunately, the Core cores are probably the least interesting element of the new design, as the Radeon RX Vega M is clearly the star of the show. It’s worth noting, though, that these new chips actually include two GPUs: Intel’s integrated Intel HD 630 GPU can process video and other less stressful video tasks, leaving the Vega M core to power up if needed.
Incorporating HBM2 was really the only clue that AMD had sold Intel a semi-custom Vega design, and not reused the older Polaris core. The two versions of the Vega M—the GH, or “Graphics High,” and the GL, or “Graphics Low”—don’t differ that much from one another. The GH uses 24 compute units and 1,536 stream processors, and boosts from 1,063 MHz to 1,190 MHz. The GL, meanwhile, includes 20 compute units and 1,280 stream processors, and boosts from 931 MHz to 1,011 MHz.
Interestingly, though the chip is called the Vega M, Intel won’t confirm that it uses the AMD Radeon Vega core. “This is a custom Radeon graphics solution built for Intel,” an Intel spokeswoman said in an email. “It is similar to the desktop Radeon RX Vega solution with a high-bandwidth memory cache controller and enhanced compute units with additional Render Output Units.”
Eight lanes of PCI Express Gen 3 connect the CPU and the GPU, an architecture designed for “intense” graphics workloads, Intel says. And all of the dies within the package are connected via the Embedded Multi-die Interconnect Bridge, the “secret sauce” that marries disparate dies into a single unit.
Intel
Both the Radeon RX Vega M core and the integrated Intel HD630 core have capabilities that complement one another.
"> Intel
Intel
Both the Radeon RX Vega M core and the integrated Intel HD630 core have capabilities that complement one another.
In comparison to AMD’s existing Ryzen parts, the new Kaby Lake-G chips far exceed their AMD rivals. The first Ryzen Mobile laptop CPUs include 10 Vega-based compute units. AMD’s dedicated, discrete GPU, the $399 Radeon RX Vega 56, uses 56 compute units. (A 28-compute unit/1,792 stream processor desktop APU is also rumored to be in the works.) All told, however, the new 8th-gen Core chips appear to pack in a ton of performance.
Intel’s Kaby Lake-G performance claims
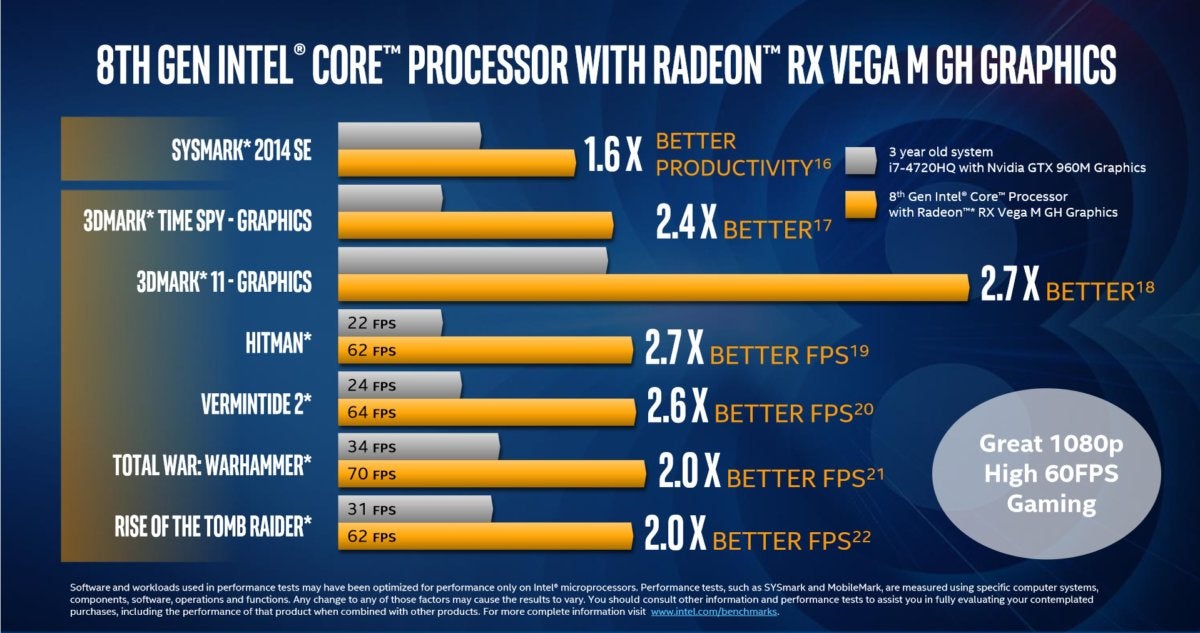
So how will Kaby Lake-G actually perform? Because Intel’s new Kaby Lake-G chip is the first of its kind, there’s not much to compare it to within Intel’s lineup. Normally, Intel compares new chips to a five-year-old PC—not that useful for our purposes. Here, though, Intel did something slightly different: It compared the RX Vega M GH core to a 3-year-old Core i7 PC with a discrete Nvidia GTX 960M card. In this face-off, the new Intel chip looks quite impressive (click to expand the chart below).
Intel
Intel makes a good case to upgrade, if you’re still stuck in the Haswell generation.
"> Intel
Intel
Intel makes a good case to upgrade, if you’re still stuck in the Haswell generation.
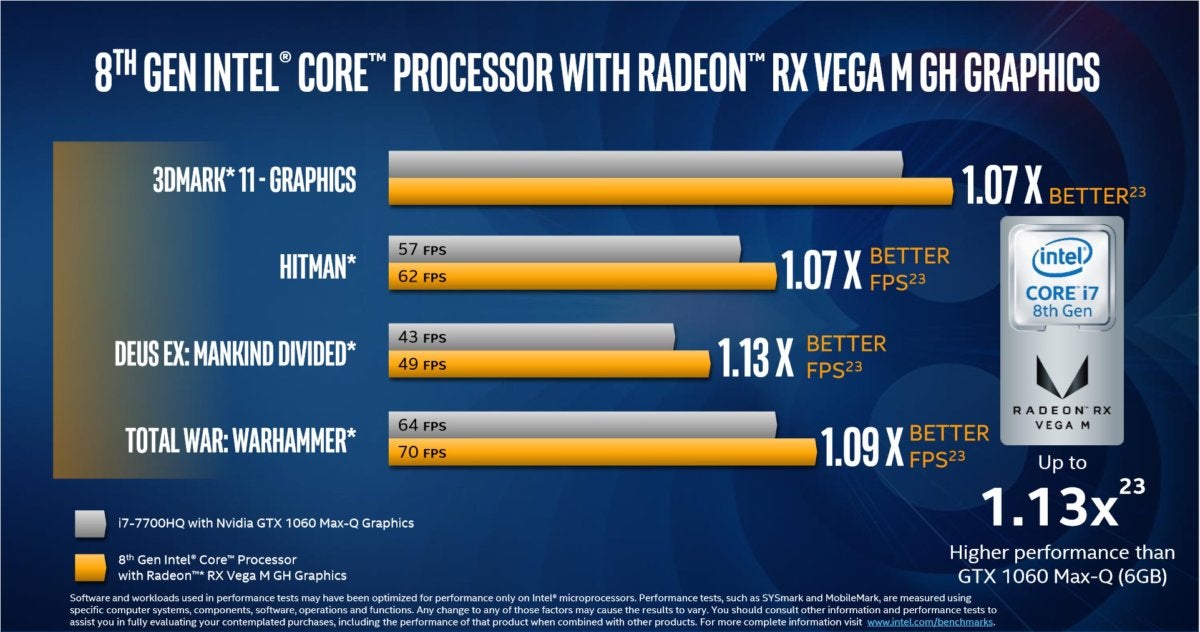
Naturally, Intel also makes its case by comparing Kaby Lake-G to the current leader in discrete Nvidia GPUs, the Nvida GTX 1060. Here, the new chip comes off surprisingly well, too, though the test is also stacked against the opposition.
Intel
Intel’s new Core i7-8809G with Radeon graphics, compared to a Core i7-7700HQ and Nvida GTX 1060. Note that the test isn’t totally comparable, as Nvidia’s chips are complemented by a 7th-generation Core i7.
"> Intel
Intel
Intel’s new Core i7-8809G with Radeon graphics, compared to a Core i7-7700HQ and Nvida GTX 1060. Note that the test isn’t totally comparable, as Nvidia’s chips are complemented by a 7th-generation Core i7.
Finally, Intel compared the slower Vega M GL against older PCs—specifically the Core i7-8550U with an Nvidia GTX 1050 chip alongside it.
Intel
Here, the deck is stacked more fairly, as two 8th-gen Core chips are being compared.
">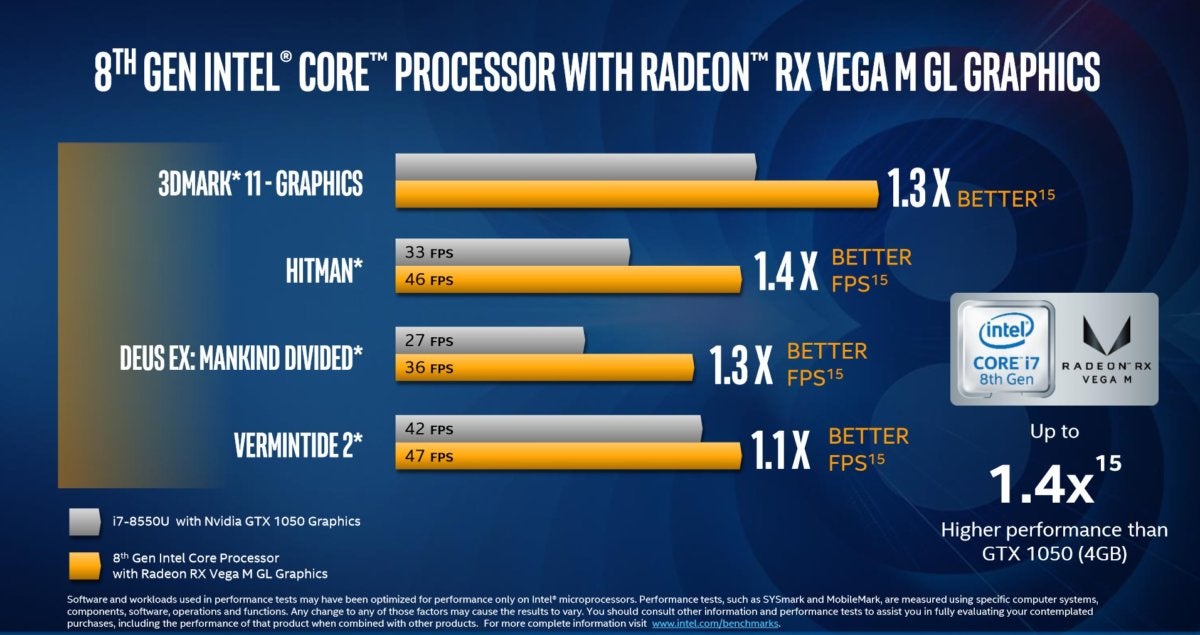 Intel
Intel
Here, the deck is stacked more fairly, as two 8th-gen Core chips are being compared.
The new chips that use Vega M GH cores are rated at 100 watts, while the GL cores are rated at 65 watts, Intel said. Intel also used a technique called dynamic tuning to power-manage all three components to improve their efficiency. That trick shoehorned in a little extra thermal headroom within the processor, so that, if needed, either the CPU or GPU could reach its respective boost speed to max out performance, all without worrying about immediately throttling down to prevent overheating.
Though the new chips include an H-series Core—that’s the version of the Core chip designed for use with any external GPU—Intel managed to squeeze them all inside of a G-series package. This helped Intel achieve the 40 percent savings in board space that the company disclosed earlier.
“We’ve only talked about one processor on 8th-gen today,” said John Webb, director of client graphics marketing at Intel. “There’s still more to come. Look for continued news on H-series [chips] as we get into 2018. I think you’ll be very excited about what’s there, as well.”
Software and drivers via Intel
Since the new Core chips with Radeon graphics represent a partnership between AMD and Intel, you can expect software support from both companies—though they will be routed through Intel. “There’s a lot of great software coming at them,” Webb said.
That means that while customers will receive AMD-specific features—Radeon Chill, Radeon ReLive, and the important FreeSync support—you can expect to see to a lot of Intel blue, as they’ll all be supplied by Intel.
Overclocking utilities—Intel XTU, and Radeon Wattman—will be supplied by their respective companies. Intel’s Webb said that Intel has committed to “Day Zero” drivers via gameplay.intel.com, too. Again, while you might expect AMD to shoulder a lot of the load here, Intel will be your source for official driver updates.
Computers from Dell, HP, Intel, and more
According to Intel, two customers will initially use the new Kaby Lake-G chips: Dell and HP. Unfortunately, Intel executives declined to go into any further detail. But because the new chips are being launched this week at the Consumer Electronics Show, we expect more announcements over the next few days.
Intel
Intel isn’t saying whether the new notebooks from HP and Dell will meet these configurations.
"> Intel
Intel
Intel isn’t saying whether the new notebooks from HP and Dell will meet these configurations.
Intel did reveal some of the specs of generic notebooks using the Radeon RX Vega M core, which you can see above. If there’s anything a little worrying, it’s that the projected weight, 4.6 pounds, looks rather heavy for an “ultrabook” form factor.
Mark Hachman / IDG
A reference notebook, of the sort that will be enhanced by the AMD-Intel partnership. The large, black blank space is designed for stylus input.
"> Mark Hachman / IDG
Mark Hachman / IDG
A reference notebook, of the sort that will be enhanced by the AMD-Intel partnership. The large, black blank space is designed for stylus input.
We can guess that both the Dell and HP notebooks will be celebrated for their VR prowess, which is also the target application of Intel’s two new NUCs, according to John Deatherage, the marketing director for Intel’s NUC products.
Intel plans to launch two models of what it calls its “Hades Canyon” NUC—aka “Next Unit of Computing”: The NUC8i7HVK, and the NUC8i7HNK, based on the Core i7-8809G and the Core i7-8705G, respectively. The full specs are below, and note that both NUCs (8.7 inches by 5.6 inches) include a pair of rear-mounted Thunderbolt 3 ports as well front- and rear-mounted HDMI ports, too.
Intel
The specs of Intel’s new NUC kits, the NUC8i7HVK and NUC8i7HNK.
">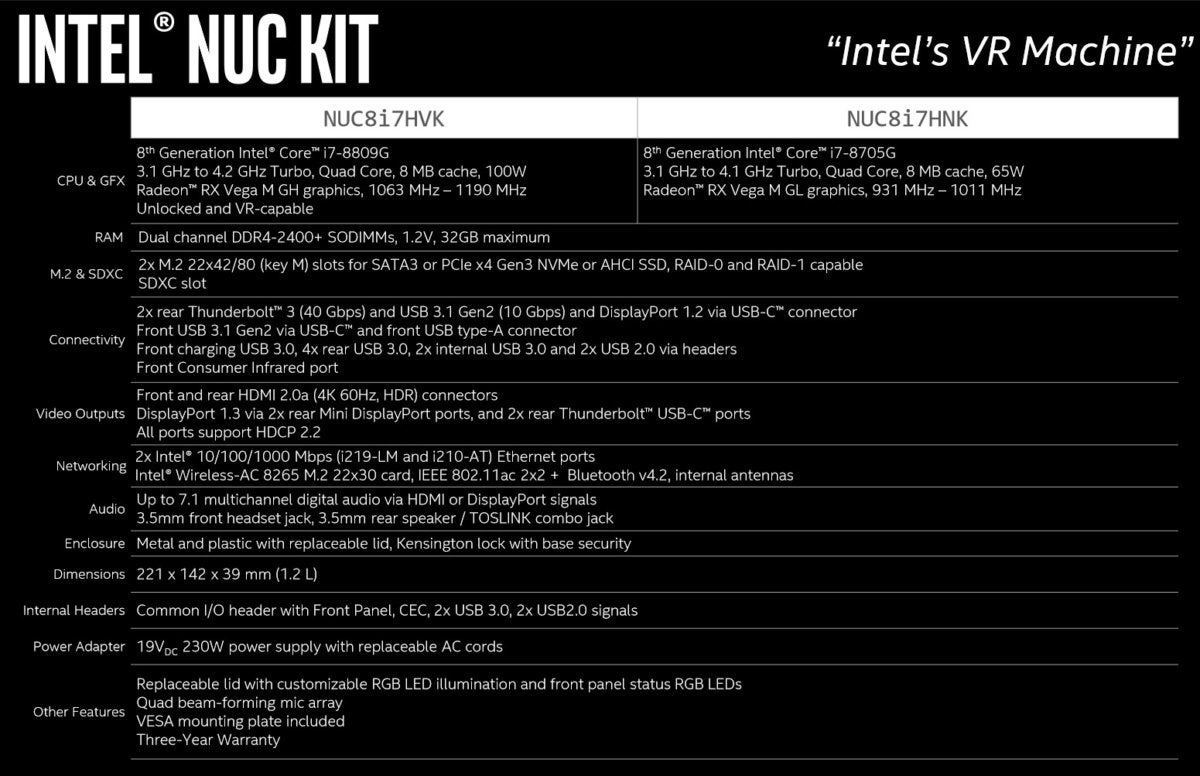 Intel
Intel
The specs of Intel’s new NUC kits, the NUC8i7HVK and NUC8i7HNK.
In fact, a closer look at the NUCs reveal that they’re literally covered in ports.
Intel
And this is just the back panel. The front adds six more, including an SD slot and headphone jack.
"> Intel
Intel
And this is just the back panel. The front adds six more, including an SD slot and headphone jack.
Finally, there’s a cool LED-lit skull that can be toggled on and off.
 Intel
Intel
“The processor and graphics will be more than you’ve ever had for NUC as well,” Deatherage added.
Both the NUC8i7HVK, and the NUC8i7HNK will begin shipping in late March, for prices that begin at $999 and $799, respectively. Fully configured systems will likely be $300 to $400 more depending on the configuration, an Intel representative said.
Naturally, it’s unclear how these new NUCs, as well as the notebooks from HP and Dell, will shape up. But if you’ve waffled between buying a traditional notebook or ultrabook with integrated graphics, or going for something a bit more powerful, Intel’s new Core-Radeon partnership sounds like it will be worth a second look. We’re looking forward to testing them out.
To comment on this article and other PCWorld content, visit our Facebook page or our Twitter feed.
Related:
As PCWorld's senior editor, Mark focuses on Microsoft news and chip technology, among other beats.
Follow
Intel launches five Core chips with Radeon graphics from rival AMD
Intel unveils the speeds, feeds, and prices of the 8th-gen Intel Core with Radeon RX Vega M graphics. The five new chips will appear in notebooks from Dell and HP, plus new Intel NUCs.
Senior Editor, PCWorld | Jan 7, 2018 6:01 PM PT

Intel
More like this
-

Intel's chip with AMD will use Radeon Vega graphics cores -

Intel and AMD team up: A future Core chip will have Radeon graphics inside -

'Hades Canyon' NUCs finally give Intel's tiny PCs the gaming chops they deserve -

Video
Intel's Kaby Lake G NUC has serious gaming chops
-

41% off CyberPower Surge Protector 3-AC Outlet with 2 USB (2.1A) Charging... -

39% off American Red Cross Blackout Buddy Emergency Nightlight - Deal Alert -

Save 90% On A Lifetime of Disconnect Premium VPN - Deal Alert
Latest Reviews
IdeaPad Miix 520
on Amazon $973.63
Life is Strange: Before the Storm
on Steam , MSRP $16.99 Learn more
Sapphire Nitro+ Radeon RX 64 Limited Edition
Intel’s startling marriage with AMD’s graphics chips has finally borne fruit, as Intel announced five new Core H-series chips that use two variants of the AMD “Vega M” GPU. The combination of Intel and AMD technology should outperform a last-gen system with a discrete Nvidia chip, Intel says.
You can jump straight to our performance section to learn more about Intel’s claims.
The new 8th-generation, quad-core Core i5 and Core i7 chips, together with what AMD calls the Radeon RX Vega M GPU, will power laptops from Dell and HP. They’ll also appear in new Intel-branded “Hades Canyon” NUCs, with prices beginning at $799 and $999, Intel said.
[ Further reading: Our picks for best PC laptops ]
Intel’s announcement Sunday at CES adds a significant amount of detail to the bombshell AMD and Intel dropped in November. Intel’s overarching goal with its Core/Radeon combination has been to deliver a gaming PC with great VR capabilities within an ultrabook form factor. We now know the NUCs will ship in late March, though timing remains unclear for the notebook launches. Intel also shared more information on speeds and feeds.
Intel originally disclosed that its new processor contained an H-series Core chip, the AMD GPU, and HBM2 memory, all within the same package. We now know the clock speeds of the five Core i5 and i7 cores will range from 3.8GHz to 4.2GHz, and that 4GB of HBM2 memory will accompany both the Vega M GH and Vega M GL, the two GPU versions whose 20 and 24 compute units appear to be much more powerful than AMD’s own Ryzen 7 and Ryzen 5 for laptops.
Intel says its new chips will be 7 percent faster in 3DMark versus a Core i7-7700HQ system with an Nvidia GTX 1060 Max-Q (6GB) chip accompanying it, and up to 13 percent faster in games.
Why this matters: For years, we’ve seen integrated notebook processors and notebook chips that use discrete GPUs, each with their own performance tier. Intel’s new partnership with AMD’s Radeon division splits the difference, offering a somewhat modular solution together with graphical performance that’s rather impressive. We all suspected that the Intel-AMD partnership would be a game-changer, and we’re starting to see that it is. We don’t know how Intel will price these chips compared to its more vanilla Core i5 and Core i7 processors, however.

Intel’s new 8th-gen Core package with a Vega M core inside of it is surprisingly photogenic.
Table of Contents
- Core plus Radeon equals power
- Intel’s Kaby Lake-G performance claims
- Software and drivers via Intel
- Computers from Dell, HP, Intel, and more
What Intel formally refers to as the “8th-gen Intel Core with Radeon RX Vega M graphics” is a typographical nightmare, so it makes more sense to either refer to them with a nickname—whatever it ends up being, Kaby Lake-G perhaps?—or simply by their actual model names. Naturally, since they’re all members of the 8th-gen Core family, all five processors boast four cores and eight processing threads.
Most notable among the new chips—which differ in processor speed, vPro capabilities, and whether they use the Vega M GH and Vega M GL—is the Core i7-8809G. That chip, leaked last week, was the first indication that Intel’s new chips would indeed include AMD’s Vega cores. It’s also the only one of the five chips that totally unlocks the CPU, GPU, and HBM.
Alongside the Core i7-8809G, though, are the Core i7-8709G, the Core i7-8706G, the 3.1Core i7-8705G, and the Core i5-8305G. As the chart below shows, they all share a common cache size (8MB), a common integrated Intel GPU (the Intel HD620), and two memory channels connecting to DDR4-2400 memory.
Intel
Intel’s five new Intel Core chips with the Radeon RX Vega M core inside. Note that they’re differentiated by clock speed, GPU core, and whether or not they have vPro capabilities. Intel did not disclose prices.
">
 Intel
IntelIntel’s five new Intel Core chips with the Radeon RX Vega M core inside. Note that they’re differentiated by clock speed, GPU core, and whether or not they have vPro capabilities. Intel did not disclose prices.
Unfortunately, the Core cores are probably the least interesting element of the new design, as the Radeon RX Vega M is clearly the star of the show. It’s worth noting, though, that these new chips actually include two GPUs: Intel’s integrated Intel HD 630 GPU can process video and other less stressful video tasks, leaving the Vega M core to power up if needed.
Incorporating HBM2 was really the only clue that AMD had sold Intel a semi-custom Vega design, and not reused the older Polaris core. The two versions of the Vega M—the GH, or “Graphics High,” and the GL, or “Graphics Low”—don’t differ that much from one another. The GH uses 24 compute units and 1,536 stream processors, and boosts from 1,063 MHz to 1,190 MHz. The GL, meanwhile, includes 20 compute units and 1,280 stream processors, and boosts from 931 MHz to 1,011 MHz.
Interestingly, though the chip is called the Vega M, Intel won’t confirm that it uses the AMD Radeon Vega core. “This is a custom Radeon graphics solution built for Intel,” an Intel spokeswoman said in an email. “It is similar to the desktop Radeon RX Vega solution with a high-bandwidth memory cache controller and enhanced compute units with additional Render Output Units.”
Eight lanes of PCI Express Gen 3 connect the CPU and the GPU, an architecture designed for “intense” graphics workloads, Intel says. And all of the dies within the package are connected via the Embedded Multi-die Interconnect Bridge, the “secret sauce” that marries disparate dies into a single unit.
Intel
Both the Radeon RX Vega M core and the integrated Intel HD630 core have capabilities that complement one another.
">
 Intel
IntelBoth the Radeon RX Vega M core and the integrated Intel HD630 core have capabilities that complement one another.
In comparison to AMD’s existing Ryzen parts, the new Kaby Lake-G chips far exceed their AMD rivals. The first Ryzen Mobile laptop CPUs include 10 Vega-based compute units. AMD’s dedicated, discrete GPU, the $399 Radeon RX Vega 56, uses 56 compute units. (A 28-compute unit/1,792 stream processor desktop APU is also rumored to be in the works.) All told, however, the new 8th-gen Core chips appear to pack in a ton of performance.
Intel’s Kaby Lake-G performance claims
So how will Kaby Lake-G actually perform? Because Intel’s new Kaby Lake-G chip is the first of its kind, there’s not much to compare it to within Intel’s lineup. Normally, Intel compares new chips to a five-year-old PC—not that useful for our purposes. Here, though, Intel did something slightly different: It compared the RX Vega M GH core to a 3-year-old Core i7 PC with a discrete Nvidia GTX 960M card. In this face-off, the new Intel chip looks quite impressive (click to expand the chart below).
Intel
Intel makes a good case to upgrade, if you’re still stuck in the Haswell generation.
">
 Intel
IntelIntel makes a good case to upgrade, if you’re still stuck in the Haswell generation.
Naturally, Intel also makes its case by comparing Kaby Lake-G to the current leader in discrete Nvidia GPUs, the Nvida GTX 1060. Here, the new chip comes off surprisingly well, too, though the test is also stacked against the opposition.
Intel
Intel’s new Core i7-8809G with Radeon graphics, compared to a Core i7-7700HQ and Nvida GTX 1060. Note that the test isn’t totally comparable, as Nvidia’s chips are complemented by a 7th-generation Core i7.
">
 Intel
IntelIntel’s new Core i7-8809G with Radeon graphics, compared to a Core i7-7700HQ and Nvida GTX 1060. Note that the test isn’t totally comparable, as Nvidia’s chips are complemented by a 7th-generation Core i7.
Finally, Intel compared the slower Vega M GL against older PCs—specifically the Core i7-8550U with an Nvidia GTX 1050 chip alongside it.
Intel
Here, the deck is stacked more fairly, as two 8th-gen Core chips are being compared.
">
 Intel
IntelHere, the deck is stacked more fairly, as two 8th-gen Core chips are being compared.
The new chips that use Vega M GH cores are rated at 100 watts, while the GL cores are rated at 65 watts, Intel said. Intel also used a technique called dynamic tuning to power-manage all three components to improve their efficiency. That trick shoehorned in a little extra thermal headroom within the processor, so that, if needed, either the CPU or GPU could reach its respective boost speed to max out performance, all without worrying about immediately throttling down to prevent overheating.
Though the new chips include an H-series Core—that’s the version of the Core chip designed for use with any external GPU—Intel managed to squeeze them all inside of a G-series package. This helped Intel achieve the 40 percent savings in board space that the company disclosed earlier.
“We’ve only talked about one processor on 8th-gen today,” said John Webb, director of client graphics marketing at Intel. “There’s still more to come. Look for continued news on H-series [chips] as we get into 2018. I think you’ll be very excited about what’s there, as well.”
Software and drivers via Intel
Since the new Core chips with Radeon graphics represent a partnership between AMD and Intel, you can expect software support from both companies—though they will be routed through Intel. “There’s a lot of great software coming at them,” Webb said.
That means that while customers will receive AMD-specific features—Radeon Chill, Radeon ReLive, and the important FreeSync support—you can expect to see to a lot of Intel blue, as they’ll all be supplied by Intel.
Overclocking utilities—Intel XTU, and Radeon Wattman—will be supplied by their respective companies. Intel’s Webb said that Intel has committed to “Day Zero” drivers via gameplay.intel.com, too. Again, while you might expect AMD to shoulder a lot of the load here, Intel will be your source for official driver updates.
Computers from Dell, HP, Intel, and more
According to Intel, two customers will initially use the new Kaby Lake-G chips: Dell and HP. Unfortunately, Intel executives declined to go into any further detail. But because the new chips are being launched this week at the Consumer Electronics Show, we expect more announcements over the next few days.
Intel
Intel isn’t saying whether the new notebooks from HP and Dell will meet these configurations.
">
 Intel
IntelIntel isn’t saying whether the new notebooks from HP and Dell will meet these configurations.
Intel did reveal some of the specs of generic notebooks using the Radeon RX Vega M core, which you can see above. If there’s anything a little worrying, it’s that the projected weight, 4.6 pounds, looks rather heavy for an “ultrabook” form factor.
Mark Hachman / IDG
A reference notebook, of the sort that will be enhanced by the AMD-Intel partnership. The large, black blank space is designed for stylus input.
">
 Mark Hachman / IDG
Mark Hachman / IDGA reference notebook, of the sort that will be enhanced by the AMD-Intel partnership. The large, black blank space is designed for stylus input.
We can guess that both the Dell and HP notebooks will be celebrated for their VR prowess, which is also the target application of Intel’s two new NUCs, according to John Deatherage, the marketing director for Intel’s NUC products.
Intel plans to launch two models of what it calls its “Hades Canyon” NUC—aka “Next Unit of Computing”: The NUC8i7HVK, and the NUC8i7HNK, based on the Core i7-8809G and the Core i7-8705G, respectively. The full specs are below, and note that both NUCs (8.7 inches by 5.6 inches) include a pair of rear-mounted Thunderbolt 3 ports as well front- and rear-mounted HDMI ports, too.
Intel
The specs of Intel’s new NUC kits, the NUC8i7HVK and NUC8i7HNK.
">
 Intel
IntelThe specs of Intel’s new NUC kits, the NUC8i7HVK and NUC8i7HNK.
In fact, a closer look at the NUCs reveal that they’re literally covered in ports.
Intel
And this is just the back panel. The front adds six more, including an SD slot and headphone jack.
">
 Intel
IntelAnd this is just the back panel. The front adds six more, including an SD slot and headphone jack.
Finally, there’s a cool LED-lit skull that can be toggled on and off.

“The processor and graphics will be more than you’ve ever had for NUC as well,” Deatherage added.
Both the NUC8i7HVK, and the NUC8i7HNK will begin shipping in late March, for prices that begin at $999 and $799, respectively. Fully configured systems will likely be $300 to $400 more depending on the configuration, an Intel representative said.
Naturally, it’s unclear how these new NUCs, as well as the notebooks from HP and Dell, will shape up. But if you’ve waffled between buying a traditional notebook or ultrabook with integrated graphics, or going for something a bit more powerful, Intel’s new Core-Radeon partnership sounds like it will be worth a second look. We’re looking forward to testing them out.
To comment on this article and other PCWorld content, visit our Facebook page or our Twitter feed.
Related:
As PCWorld's senior editor, Mark focuses on Microsoft news and chip technology, among other beats.
Follow