- Joined
- Aug 20, 2022
- Messages
- 26,005
- Points
- 113
Ransomed.vc group claims hack on “all of Sony systems”
www.cybersecurityconnect.com.au
 Relative ransomware newcomers have claimed to have succeeded in what could be a devastating ransomware attack on global entertainment giant Sony.
Relative ransomware newcomers have claimed to have succeeded in what could be a devastating ransomware attack on global entertainment giant Sony.
Ransomed.vc has only been operating since September, despite some links to previous forums and groups. However, in that time the group has racked up an impressive amount of victims – and Sony is one of them.
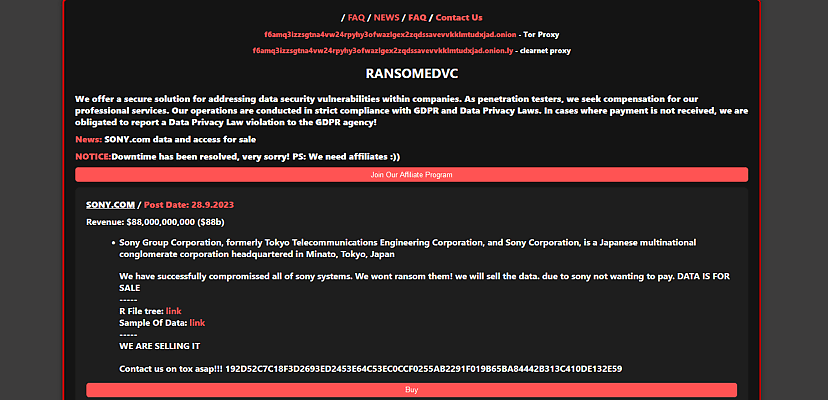
“Sony Group Corporation, formerly Tokyo Telecommunications Engineering Corporation, and Sony Corporation, is a Japanese multinational conglomerate corporation headquartered in Minato, Tokyo, Japan,” Ransomed.vc said on its leak sites, both on the clear and dark nets, taking a description straight from Wikipedia.
“We have successfully compromissed [sic] all of sony systems. We wont ransom them! we will sell the data. due to sony not wanting to pay. DATA IS FOR SALE,” the group adds, before declaring “WE ARE SELLING IT”.
The group does include some proof-of-hack data, but it’s not particularly compelling information on the face of things – there appear to be screenshots of an internal log-in page, an internal PowerPoint presentation outlining testbench details, and a number of Java files.





 Ransomed.vc has also posted a file tree of the entire leak, which appears to have less than 6,000 files – seemingly small for “all of Sony systems”. Included here “build log files”, a wide range of Java resources, and HTML files.
Ransomed.vc has also posted a file tree of the entire leak, which appears to have less than 6,000 files – seemingly small for “all of Sony systems”. Included here “build log files”, a wide range of Java resources, and HTML files.
Many of the sample files appear to feature Japanese characters prominently.
No price is listed for the data, but Ransomed.vc has left contact details for the Tox messaging service, as well as Telegram and email details.
VIEW ALL
 Listen to the latest Cyber Security Connect podcast! READ MORE
Listen to the latest Cyber Security Connect podcast! READ MORE

 Minimise your mortgage repayments today READ MORE
Minimise your mortgage repayments today READ MORE
 The group has also listed a “post date” of September 28 2023. If no one purchases the data, this is presumably when Ransomed.vc will publish it wholesale.
The group has also listed a “post date” of September 28 2023. If no one purchases the data, this is presumably when Ransomed.vc will publish it wholesale.
As of writing, Sony has not made any mention of a possible hack on its websites, and we have reached out in writing for confirmation of any cyber incident.
Ransomed.vc appears to be both a ransomware operator in its own right, and a ransomware-as-a-service organisation – it is currently advertising for “affiliates” to sign up.
It is also unique in its approach to ransomware in general, claiming not only to be a “secure solution for addressing data security vulnerabilities within companies”, but also to be operating “in strict compliance with GDPR and Data Privacy Laws”.
“In cases where payment is not received, we are obligated to report a Data Privacy Law violation to the GDPR agency!” the group says on its leak site.

www.cybersecurityconnect.com.au

Ransomed.vc has only been operating since September, despite some links to previous forums and groups. However, in that time the group has racked up an impressive amount of victims – and Sony is one of them.
“Sony Group Corporation, formerly Tokyo Telecommunications Engineering Corporation, and Sony Corporation, is a Japanese multinational conglomerate corporation headquartered in Minato, Tokyo, Japan,” Ransomed.vc said on its leak sites, both on the clear and dark nets, taking a description straight from Wikipedia.
“We have successfully compromissed [sic] all of sony systems. We wont ransom them! we will sell the data. due to sony not wanting to pay. DATA IS FOR SALE,” the group adds, before declaring “WE ARE SELLING IT”.
The group does include some proof-of-hack data, but it’s not particularly compelling information on the face of things – there appear to be screenshots of an internal log-in page, an internal PowerPoint presentation outlining testbench details, and a number of Java files.





Many of the sample files appear to feature Japanese characters prominently.
No price is listed for the data, but Ransomed.vc has left contact details for the Tox messaging service, as well as Telegram and email details.
VIEW ALL




As of writing, Sony has not made any mention of a possible hack on its websites, and we have reached out in writing for confirmation of any cyber incident.
Ransomed.vc appears to be both a ransomware operator in its own right, and a ransomware-as-a-service organisation – it is currently advertising for “affiliates” to sign up.
It is also unique in its approach to ransomware in general, claiming not only to be a “secure solution for addressing data security vulnerabilities within companies”, but also to be operating “in strict compliance with GDPR and Data Privacy Laws”.
“In cases where payment is not received, we are obligated to report a Data Privacy Law violation to the GDPR agency!” the group says on its leak site.

