-
IP addresses are NOT logged in this forum so there's no point asking. Please note that this forum is full of homophobes, racists, lunatics, schizophrenics & absolute nut jobs with a smattering of geniuses, Chinese chauvinists, Moderate Muslims and last but not least a couple of "know-it-alls" constantly sprouting their dubious wisdom. If you believe that content generated by unsavory characters might cause you offense PLEASE LEAVE NOW! Sammyboy Admin and Staff are not responsible for your hurt feelings should you choose to read any of the content here. The OTHER forum is HERE so please stop asking.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
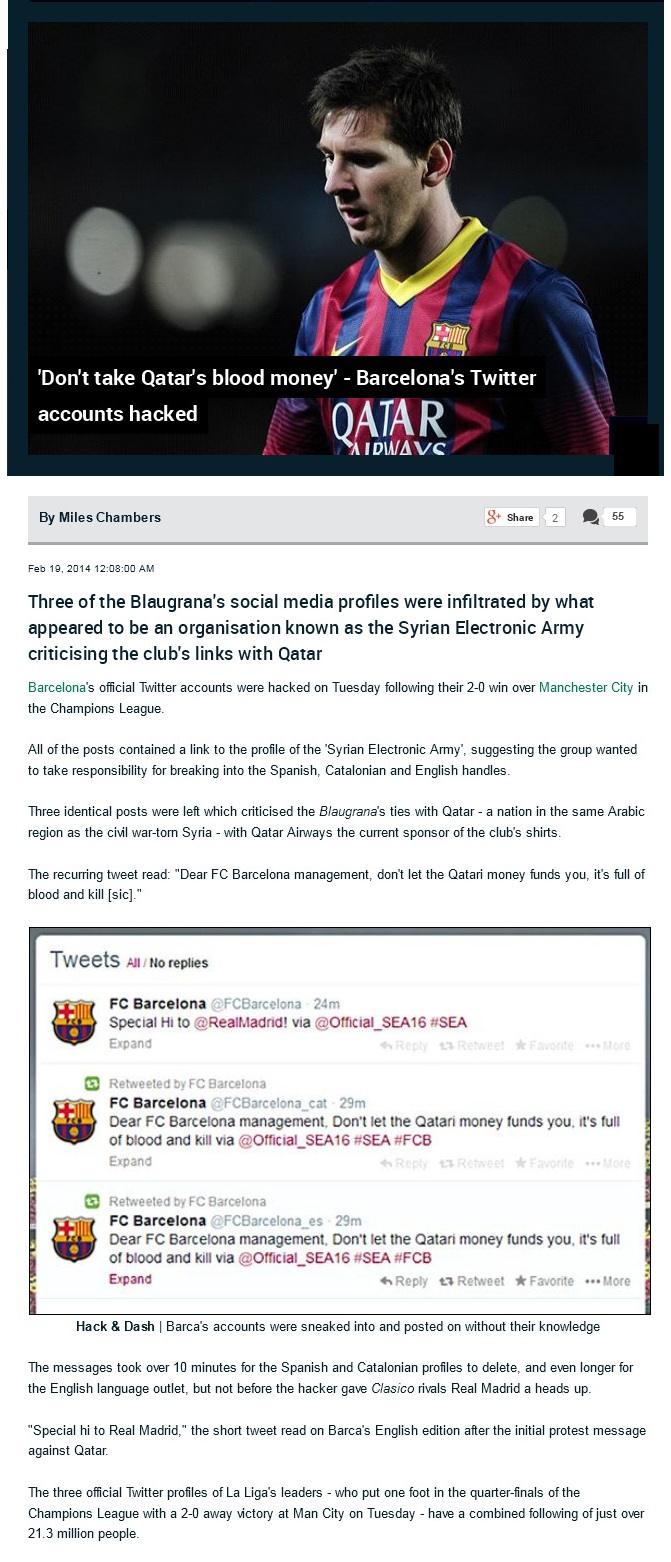
Hacking 101
- Thread starter General Grievous
- Start date
Iranian Hackers Penetrated US Navy Marine Corps Internet for Four Months

Iranian Hackers Penetrated US Navy Marine Corps Internet for Four Months Vice Adm. Michael Rogers
Tuesday, 18 Feb 2014 06:28 AM
By Elliot Jager
Iranian hackers were able to penetrate the Navy Marine Corps Internet for four months, monitoring the unclassified voice, video, and data communications of the network's 800,000 users around the world, The Wall Street Journal reported.
The breach, which left Iranian spyware lurking throughout the system, was deeper and longer than previously thought, according to the newspaper. Officials said they had initially underestimated the skills of the Iranian hackers.
No email accounts were hacked, the Navy said.
The penetration will probably be probed during the confirmation hearings of Vice Adm. Michael Rogers, whom President Barack Obama has nominated to become director of the National Security Agency. As head of Fleet Cyber Command, Rogers is chief of cybersecurity and oversaw the Navy's response to the Iranian cyberattack, according to the Journal.
Navy sources said it took four months, until November 2013, to drive the invasive hackers from the computer network because it was a significant penetration that capitalized on a weakness in a public-facing website. The sources added that the Navy took its time because it wanted to fix the underlying security weak spots, not just this particular infiltration.
A defense source told the Journal that Rogers did a good job handling the infiltration. "It was a big problem, but it was a success," said the official. The incident is not expected to spoil Rogers' confirmation prospects.
The cyberattack cost the Navy at least $10 million to patch. Broader defenses put in place at the Defense Department will likely cost several hundred million dollars more, the Journal reported.
Obama selected Rogers for the NSA post because of his background in cyberwarfare, according to The New York Times. It is not known if he was involved in the Stuxnet sabotage operation aimed at thwarting Iran's nuclear weapons program.
Next Media's websites hacked
Central News Agency
2014-02-22 07:25 PM
Taipei, Feb. 22 (CNA) Next Media Ltd. said Saturday that its websites for Hong Kong and Taiwan readers were both attacked by hackers and that services have not yet been fully restored.
Taiwan's Apple Daily website has been experiencing unstable Internet connection since 1 p.m. and the situation has not improved, the company said in a report date stamped 5:34 p.m.
The company also posted messages on its Facebook page, apologizing to its readers.
Technicians have been doing their best to fix the problem since the attack was discovered, the company said.
(By Sabine Cheng and James Lee)
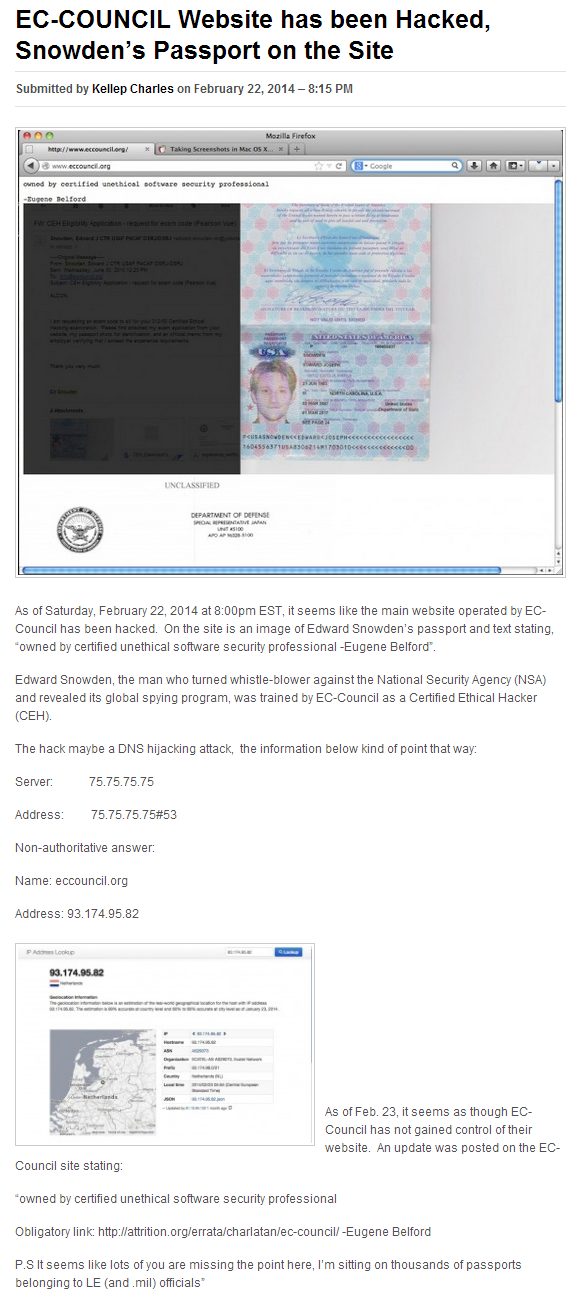


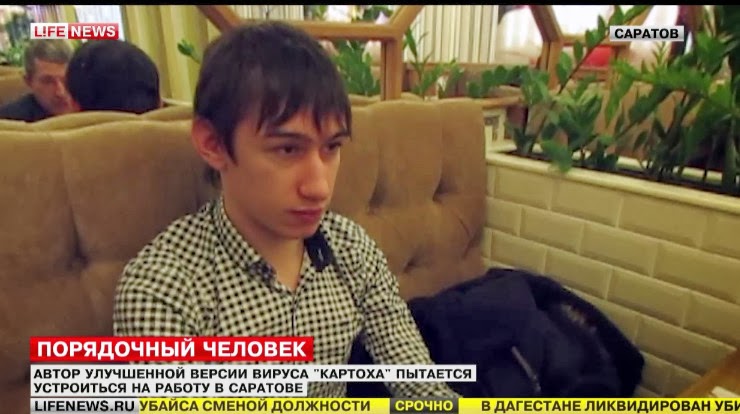
Russian Hacker Rinat Shabayev admits to be creator of BlackPOS Malware
by Sabari Selvan on Wednesday, January 22, 2014
Last week, cyber security firm IntelCrawler named the 17-year-old Russian "Sergey Taraspov" as creator of the BlackPOS Malware which was used in the Target data breach.
After further investigation, the company update its report saying that 23-year-old Russian hacker named "Rinat Shibaev" is the original author of this malware and Sergey is member of technical support team.
In an interview with Russian news channel LifeNews, Shibaev has admitted that he had developed the BlackPOS(also referred as Kaptoxa) malware.
The hacker says he just took readily available program and developed it with additional features.
He allegedly got help in developing the malware from an unknown person whom he had met online. However, he said that he doesn't even know in which country the person lives.
The hacker also said that he created it for selling it to others, not to use the application by himself.
Wi-Fi computer virus goes ‘airborne’ like common cold
Published time: February 26, 2014 20:25
Edited time: February 27, 2014 04:20

Reuters / Keith Bedford
Researchers in Britain have shown for the first time how a computer virus can spread through Wi-Fi “as efficiently as the common cold spreads between humans.” The 'Chameleon’ Wi-Fi AP-AP virus infiltrates dense networks and spreads at an alarming rate.
Chameleon was designed by a team of researchers from the University of Liverpool, and displayed a ‘remarkable amount of intelligence’ in its capacity to spread in a similar way to the common cold.
The virus “was able to avoid detection and identify the points at which Wi-Fi access is least protected by encryption and passwords,” according to a release published on the university’s website. The areas which are generally ‘least protected’ are public access points – such as free Wi-Fi in cafes and airports.
Network Security Professor, Alan Marshall, stated that the virus doesn’t attempt to damage existing networks but instead infiltrates the data of all users connected to a network via Wi-Fi .
“WiFi connections are increasingly a target for computer hackers because of well-documented security vulnerabilities, which make it difficult to detect and defend against a virus,” said Marshall.
“It was assumed, however, that it wasn’t possible to develop a virus that could attack Wi-Fi networks but we demonstrated that this is possible and that it can spread quickly. We are now able to use the data generated from this study to develop a new technique to identify when an attack is likely,” he added.
Chameleon’s success lies in the means by which it avoids detection – the majority of anti-virus software packages looks for infections which are present on computers and the Internet, rather than publicly-used Wi-Fi networks.
“When Chameleon attacked an AP (access point) it didn’t affect how it worked, but was able to collect and report the credentials of all other Wi-Fi users who connected to it. The virus then sought out other Wi-Fi APs that it could connect to and infect,” Marshall said. That the virus doesn’t disrupt the network itself, but instead those connecting to it, makes it all the more subversive and dangerous.
The virus was found to travel the most quickly between access points which were within a distance of 160 feet, prompting the ‘common cold’ comparison.
“As demand drives up the availability and use of WiFi, the geographical area that an attack can exploit increases exponentially,” the study noted.
There are plans in place to examine the data generated by the study “to develop a new technique to identify when an attack is likely,” according to Marshall.
Hong Kong University falls victim to cyberattack
E-mail accounts and personal websites belonging to staff and students targeted in attack
PUBLISHED : Saturday, 01 March, 2014, 10:58am
UPDATED : Saturday, 01 March, 2014, 1:11pm
SCMP staff
A screenshot of HKU's website
The University of Hong Kong has fallen victim to hackers for the second time in just a few months, with 40 personal websites and 150 e-mail accounts belonging to students and teaching staff targeted, local media reported on Saturday.
The attack is the latest in a string of hacks to make headlines, including one on the university in July which targeted thousands of online accounts, and an attack on Macau government e-mail accounts.
The security breach in Macau was believed to have been carried out by hackers in both Hong Kong and the United States..
A total of 3,676 e-mail accounts belonging to students and teaching staff at HKU were compromised in the July attack, SCMP reported.
HKU said they did not know who the hackers were, and they had reported the case to the police, according to reports.
It was not yet clear if the attack was connected with previous security breaches.
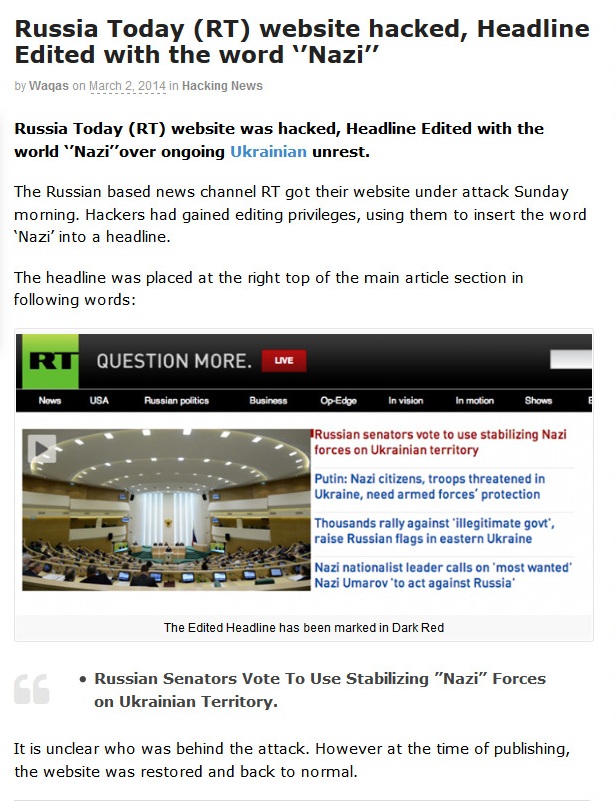
Anonymous Declares Cyberwar on Countries Found Disturbing Peace in Ukraine
by Waqas on February 28, 2014

The online Anonymous Hacktivist has released a video message in which it has declared cyberwar on countries and organizations, posing a threat to freedom and independence of Ukraine. The operation has been named as ”Operation Ukraine” (#OpIndependence).
<iframe src="//www.youtube.com/embed/1AWEI9rFYXs?rel=0" allowfullscreen="" frameborder="0" height="315" width="560"></iframe>
A 4:37 minute video message highlights several aspects of Ukrainian crisis such as international interference and divided mindset of Anonymous collective over the issue.
This is sad as some Anons are unknowingly supporting the dark forces at work in Ukraine. Members of Anonymous Ukraine are aware of the internal meddling by the United States, NATO and the European Union into the internal sovereign affairs of Ukraine.
Anonymous Ukraine claims that the country doesn’t need to join European Union nor the NATO on their territory. The message also highlights Nazi role in the crisis.
"The people of Ukraine do not want European Union integration. The people of Ukraine do not want NATO on their territory. The Bandera Nazis and fascist thugs that are beating and killing police and members of the security services of Ukraine do not represent the will or the wishes of the people of Ukraine."
Anonymous has vowed to expose West and Ukrainian opposition as it did last February when it hacked and leaked secret email conversations of Vitali Klitschko’s UDAR opposition party. You can read the leaked emails here.
Anonymous Ukraine has released the e-mails of one of the leaders of the so called opposition and will continue to expose the moves by the west to subvert the sovereign country of Ukraine.
Hacktivists have urged the Ukrainian President Yanukovich, to restore order and bring calm and stability in the country. The message ends with a declaration in which Anonymous Ukraine has declared cyberwar on countries and organizations posing threat to freedom and independence of Ukraine.
"We appeal to the president of our country. The people of Ukraine urge you. President Yanukovich, to restore order and bring calm and stability. Anonymous Ukraine will strike at all of the web resources of western hirelings and fascists. We declare the continuation of Operation Independence. We will strike at the web resources of countries and organizations that pose a threat to freedom and independence of Ukraine!"
Briton 'hacked US banking system'

Lauri Love who has been charged with hacking into American computer systems.
28 FEBRUARY 2014
A British man has been charged with hacking into US Federal Reserve computer servers and stealing sensitive personal information of users.
Lauri Love, 28, has been charged with computer hacking and aggravated identity theft, which carry a potential penalty of up to 12 years in prison, the Federal Bureau of Investigation (FBI) said.
The allegations were made in an indictment that was revealed in Manhattan federal court.
He has been charged with one count of computer hacking, which carries a maximum term of 10 years in prison and one count of aggravated identity theft, which carries an additional two-year prison sentence.
US Attorney Preet Bharara claimed Love was "a sophisticated hacker who broke into Federal Reserve computers, stole sensitive personal information, and made it widely available, leaving people vulnerable to malicious use of that information".
It is claimed the offences date from October 2012 to February 2013 when Love tried to secretly infiltrate the New York Federal Reserve Bank's computer servers in order to steal non-public information and then post that information on certain websites.
It is alleged that Love, of Stradishall, Suffolk, worked with "other hackers around the world to gain access". They were trying to target a software programme which "contained a vulnerability" in order to break in to the servers, it was claimed.
In October 2012, according to the indictment: "Love used his unauthorised access to locate and steal certain confidential information residing on the Federal Reserve servers, including the names, email addresses, and phone numbers of users of the Federal Reserve computer system. Love then disseminated that information publicly by posting the information to a website that previously had been hacked and that he controlled".
George Venizelos, head of the New York office of the FBI, said: "Cyber-crime knows no boundaries and justice will not stop at international borders."
The US authorities previously said he was charged with hacking into thousands of American computer systems including the US army, Nasa and other federal agencies.
Love is accused of breaching the systems to steal "massive quantities" of confidential data resulting in millions of dollars of losses. He was arrested by officers from the UK's National Crime Agency (NCA) under the Computer Misuse Act (CMA) in October last year and later charged by US authorities in New Jersey.
Under the CMA, individuals can be arrested for launching attacks from within the UK against computers anywhere in the world.
He and co-conspirators - believed to be in Australia and Sweden - allegedly created "back doors" into government networks, allowing them to return to get data.
Love has taken part in protests for Occupy, the global "anti-greed movement" and h is father Alexander Love, 60, a Baptist minister, works as a chaplain at HMP Highpoint North. His mother Sirkka-Liisa Love, 59, also works at the jail as a teacher.
850,000 bitcoins lost as Mt Gox exchange files for bankruptcy
Bowing in contrition, Mt Gox chief executive Mark Karpeles apologises for troubles and blames lax internal computer security systems
PUBLISHED : Friday, 28 February, 2014, 7:04pm
UPDATED : Saturday, 01 March, 2014, 8:32am
Danny Lee and Agencies [email protected]

Mt Gox chief executive Mark Karpeles looks resigned as he appears in front of the cameras in Tokyo. Photo: Reuters

Protesters hold placards as they demonstrate outside Mt Gox offices in Tokyo. Photo: Reuters
Troubled bitcoin business Mt Gox yesterday filed for bankruptcy, ending days of speculation about the Tokyo-based company's dire financial situation.
At a press conference at Tokyo District Court, Mt Gox's French CEO Mark Karpeles said the firm had applied for bankruptcy protection as it was saddled with 6.5 billion yen (HK$494 million) in outstanding debt and only 3.8 billion yen in assets to cover losses.
A bigger black hole for investors may yet emerge as Mt Gox said the exchange, used overwhelmingly by foreigners, had lost 750,000 of its users' bitcoins and 100,000 of its own. At the current bitcoin price of about US$565, that would total some US$476 million.
Just hours before the bankruptcy filing, Japanese Finance Minister Taro Aso said: "No one recognises them as a real currency. I expected such a thing to collapse."
Japan's financial regulators have been reluctant to intervene in the Mt Gox situation, saying they do not have jurisdiction over something that is not a real currency.
An embattled Karpeles looked tired and resigned as he appeared in front of the cameras.
Bowing in contrition, Karpeles spoke in Japanese and said: "I am sorry for the troubles I have caused all the people." He apologised for what he cited as "a weakness in our system", pointing a finger at lax internal computer security systems.
Once a major mover and shaker in the virtual currency world, problems began to emerge on February 7 when Mt Gox suspended bitcoin withdrawals.
After weeks of turmoil, a loss on a grand scale began to emerge after a leaked company document pointed to a huge theft of its custodial bitcoins, but Mt Gox remained largely silent.
Mt Gox said it had only found out about the missing bitcoins only last Monday, at which point the company halted all transactions. The cost per bitcoin dropped 5 per cent to US$557.17 after the bankruptcy announcement was made. The negative reaction is considered modest after the leaked Mt Gox document contributed to a 25 per cent drop in price.
The insolvency strategy deals a hammer blow to bitcoin, seeking to become an alternative to real-world cash.
Nathaniel Karp, the chief US economist at Spanish banking group BBVA research, described the Mt Gox situation as "a costly and big confidence blow that will have a more prolonged impact".
He added: "Bitcoin is not the beginning nor the end of the virtual currency saga."
The loss raises questions around the current lack of consumer protection in the rising popularity of virtual currencies.
In Hong Kong, authorities have warned consumers from buying and investing in the virtual currency, describing it as "risky" while ruling out legislation or regulation to bring it into line with other financial instruments.
Many bitcoin market participants have said Mt Gox's problems were specific to the company and were caused by what they said was a lax attitude by Karpeles, while bitcoin itself - free of any central bank control - was still a noble venture.
Bitcoin first emerged in 2008, created by a person or a team of programmers under the pseudonym Satoshi Nakamoto. The digital currency is a decentralised crypto-currency and not backed by a government or a central bank.
Bloomberg and Reuters
Second Bitcoin bank folds after hackers steal virtual cash from online vault
Digital currency comes under increasing pressure as second bank says it has closed following the theft of its bitcoin reserves
PUBLISHED : Wednesday, 05 March, 2014, 9:52am
UPDATED : Wednesday, 05 March, 2014, 10:51am
Associated Press in San Francisco, Agence France-Press in Tokyo

A Bitcoin logo on a display at the opening ceremony of the first Bitcoin counter in Hong Kong, in February. Photo: EPA
A Canada-based bank specialising in bitcoins says it has closed after computer hackers stole its digital currency.
The closure of the Flexcoin bank comes just a week after the collapse of Mt Gox, a major bitcoin exchange. Tokyo-based Mt Gox also linked its demise to an electronic heist.
The twin failures of Mt Gox and Flexcoin will probably raise more doubts about bitcoin’s ability to establish itself as an alternative currency.
In a notice on Tuesday, Flexcoin says 896 bitcoins were stolen from its online vault. That translates into a loss of about US$600,000, based on bitcoin’s current trading value.
Unlike banks dealing in government-backed currencies, Flexcoin’s losses aren’t covered by deposit insurance. The Alberta, Canada, bank says it can’t recover from the setback.
Flexcoin says bitcoins stored offline remain secure.
Mt Gox, which at one time reportedly processed 80 per cent of global bitcoin transactions, sought bankruptcy protection from the Tokyo District Court earlier this month and admitted that it had lost half a billion US dollars worth of the digital currency.
A company lawyer for Mt Gox said 750,000 bitcoins belonging to customers had gone missing, along with the company’s own store of around 100,000 units. That number of bitcoins would be worth around US$575 million.
The collapse of Flexcoin comes as regulators around the world grapple with the cryptocurrency, which is generated by complex chains of interaction among a huge network of computers.
US Federal Reserve head Janet Yellen has said the Fed has no powers over a currency that only exists virtually and has no central authority behind it.
Several countries, including Russia and China, have already heavily restricted how bitcoins can be used.
The global virtual currency community was shaken by the closure of Mt Gox, which had frozen withdrawals in early February because of what the firm said was a bug in the software underpinning bitcoin that allowed hackers to pilfer them.
Supporters rallied round, insisting bitcoin itself was sound and the problems were with Mt Gox, which they said was badly managed and unable to cope with the burgeoning popularity of the young currency.
Mt Gox’s woes depressed the global value of bitcoin and the collapse of Flexcoin is likely to further undermine it.
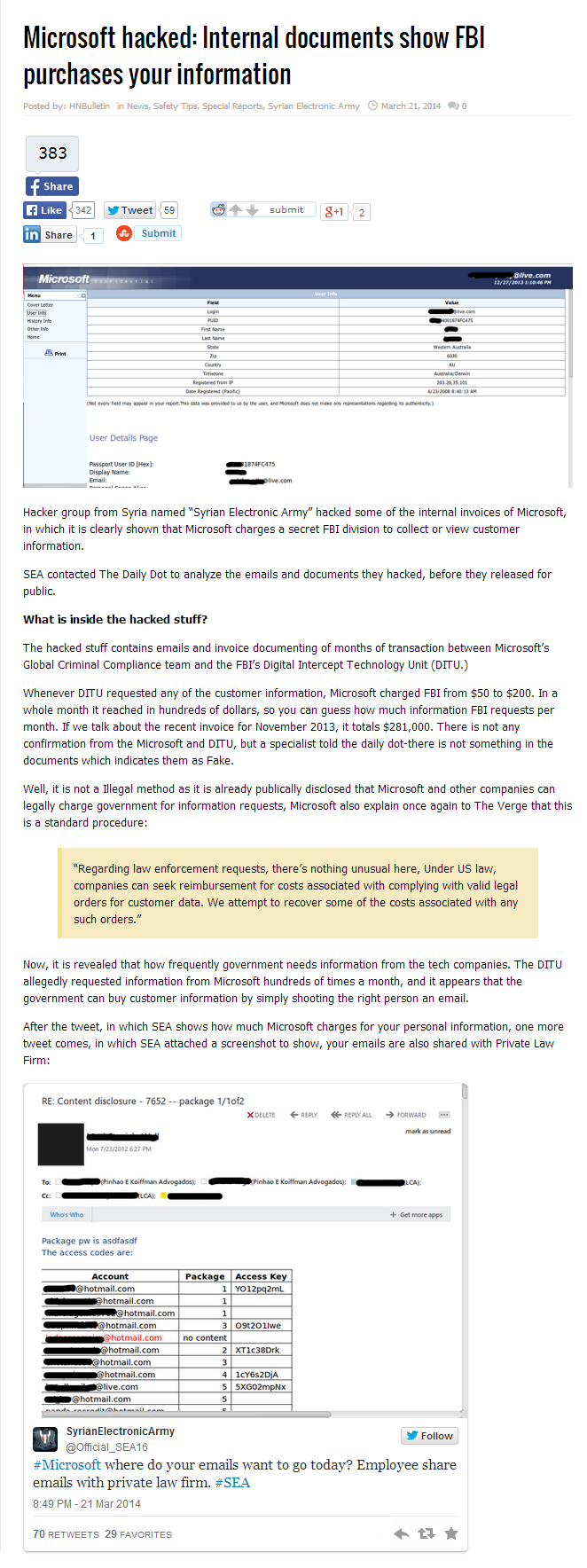
Hackers steal 12m KT users’ information
Published: 2014-03-06 21:13
Updated: 2014-03-06 21:13

A man walks in front of KT Corp.’s office in Seoul on Thursday. (Yonhap)
The Incheon Metropolitan Police Agency on Thursday arrested two hackers and a telemarketing firm CEO in connection with the theft of 12 million KT Corp. customers’ personal information.
KT is the country’s second largest telecom services provider with some 16 million consumers subscribing to its mobile, fixed-line telephone and internet services.
“KT will fully cooperate with the police investigation. (The company) will work to minimize the damage to customers.” KT said in a statement.
According to the police, the hackers, identified by the surnames Kim and Chung, had been stealing user personal information from KT since February 2013. Using a random number generating program, the hackers matched KT customer identification numbers to steal as many has 300,000 pieces of information on a daily basis.
The stolen data is said to include names, citizen registration numbers, mobile phone numbers, home addresses, occupations and bank account numbers.
Chung and Kim sold the information to the telemarketing company chief, identified by the surname Park. Park then used the information in marketing mobile telecom services, generating an estimated 11.5 billion won ($10.8 million) in illegal gains.
Park also sold the personal information of about 5 million people to three mobile phone sellers.
According to the police, the hackers received 5,000 won while Park generated between 200,000 won and 400,000 won in operating profit for each mobile phone contract sold through the scheme.
The suspects are reported to have planned to steal information from two securities companies.
The case comes while the country continues to reel from the massive data security breach at three local credit card companies.
On Jan. 8, personal information of more than 20 million KB Kookmin, NH NongHyup and Lotte card users was found to have been leaked. Following the case, a string of bills aimed at reinforcing data protection were processed by the National Assembly, while the government handed out fines and placed the three companies under a three-month operating ban.
By Choi He-suk ([email protected])
Romanian Man Commits Suicide and Kills His 4-Year-Old after Falling for Police Ransomware
A Romanian man committed suicide and killed his 4-year-old son after falling for a police ransomware scam that threatened him with huge fines and jail for watching online pornography, according to local newspaper Braila 24. This is reportedly the first murder-suicide caused by malware writers.
Before hanging himself in the living room along with his son Nicusor, the 36 year-old left a suicide note.
“I received a warning [on my computer] that said I have to pay 70.000 lei [$22,000] or go to prison for 11 years,” the note allegedly reads. “I don’t think it’s normal what I’ve done…I apologize to all of you…I don’t want Nicusor to suffer because of me…I can’t stand going to prison. I can’t.”
Bitdefender has been providing a free removal tool for Trojan.Ransom.IcePol since November 2012. The antivirus software company worked closely with Romanian police and discovered that cyber-criminals made almost $160,000 in a single year from a Romania-based server. While most of the ransom money was paid by US-based users (over $32,000), a significant percentage was also gathered from Romanian PCs ($2,500).
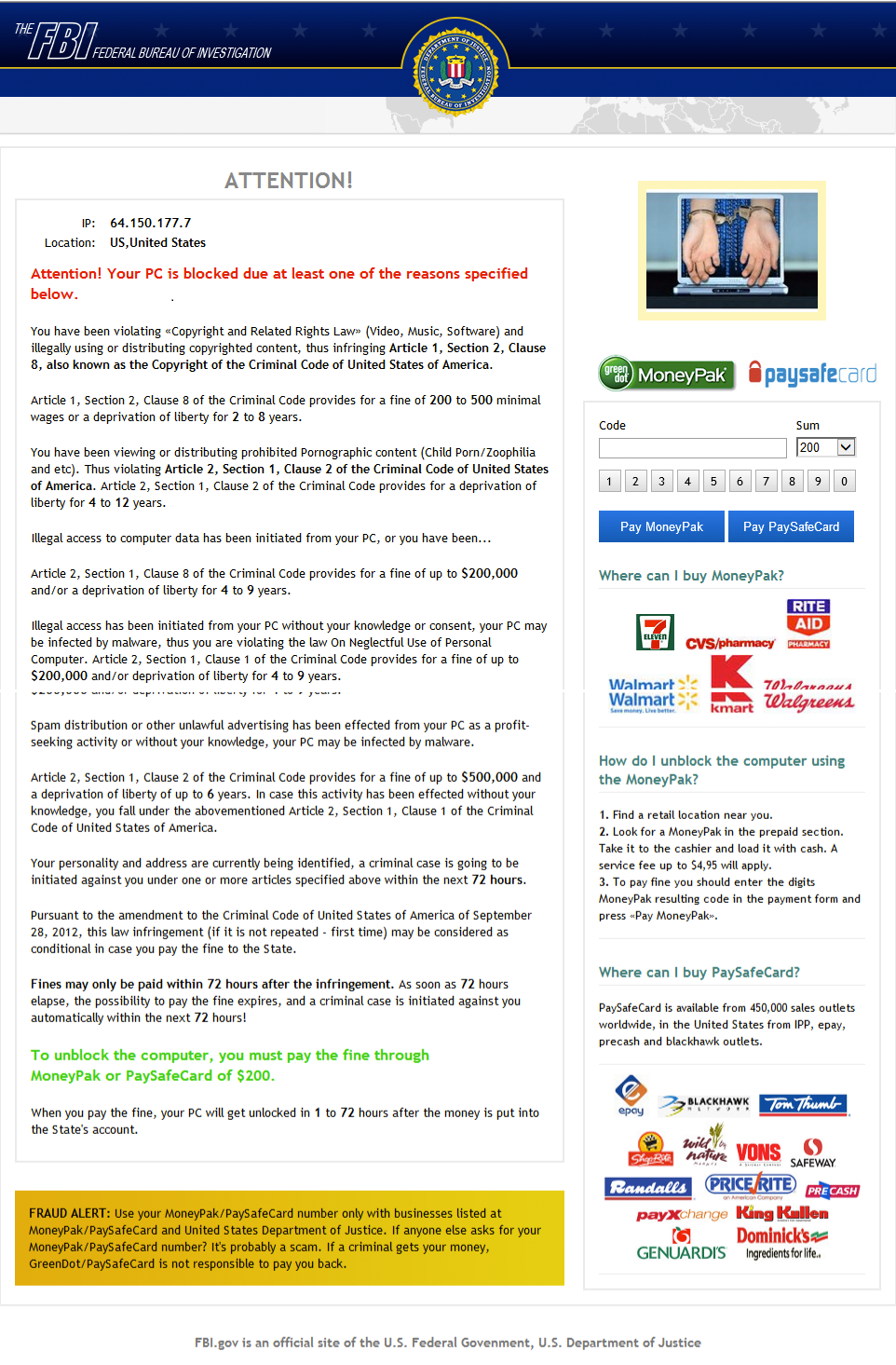
Globally, financial losses are a lot higher. In February 2013, Spanish police arrested 10 people allegedly involved in a massive “ransomware” cyber-crime organization. Authorities estimated that the ring infected tens of thousands of users worldwide, stealing over 1 million euros a year.
Ransomware is a commercial form of malware that can infect computers through spam emails or malicious websites, claiming payment to unlock the devices.
The IcePol Trojan capitalizes on people’s fear, scans their IP address and delivers a fake Police message in their native language. Phony accusations range from zoophilia and child pornography to copyright infringement.
Last edited:
Similar threads
- Replies
- 3
- Views
- 287
- Replies
- 10
- Views
- 706
- Replies
- 69
- Views
- 3K