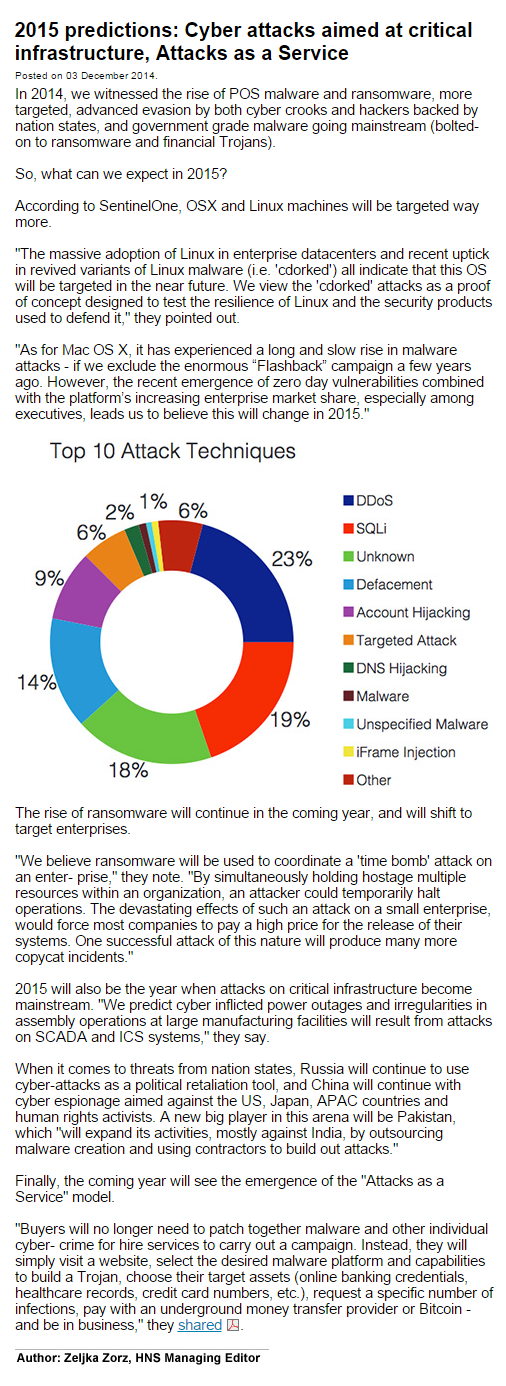
100k+ WP websites compromised by SoakSoak malware
Posted on 15 December 2014.
Sucuri Security researchers are warning about a massive compromise of WordPress sites sporting malicious JavaScript leading visitors to malware.
The discovery was made on Sunday, when Google blacklisted over compromised 11,000 domains. After poking around a bit, the researchers discovered that most of the affected hosts are running WordPress.
They believe that the compromise was the result of the exploitation of a patched vulnerability in the Slider Revolution Premium plug-in.
The SoakSoak malware, dubbed this way because it's pulled from the SoakSoak.ru website, modifies the wp-includes/template-loader.php file to include a JavaScript that causes wp-includes/js/swobject.js to be loaded on every page a visitor views on the site.
The object in question contains a Java-encoded script malware (hxxp://soaksoak.ru/xteas/code) which, when loaded, redirects users to the SoakSoak.ru website and may silently download malware.
How come website owners haven't patched that vulnerability? Those who update their plug-ins regularly did, and those that bought the plug-in directly from the developer have been kept safe by the auto-updater.
Unfortunately, the plug-in is also wrapped into theme packages, and this is where the auto-updater doesn't work. Add to this the fact that the vulnerability has been patched silently, and you get a lot of users that don't even know about it.
Sucuri researchers are urging site administrators to check whether their sites have been compromised with this or other malware via their free website malware and security scanner.